How To?
Implement authentication with FIDO2 keys
This article describes how to implement authentication with FIDO2 biometric security keys in cyberelements.
The content of this documentation is valid for any FIDO2 security key, although this article presents how to add and use a Yubikey, a security key from Yubico.
The principle of use is to allow key enrolment by the owner directly from the cyberelements web interface, in full autonomy.
Initial configuration
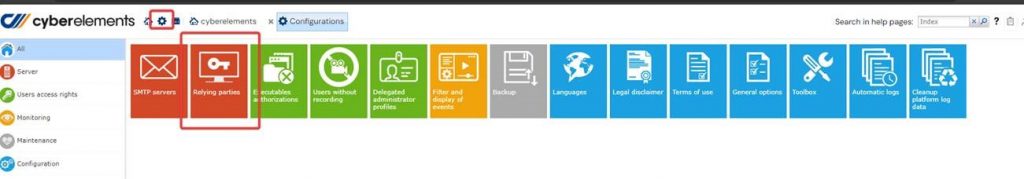
Step 1- Open the Configuration page
Enrolling keys
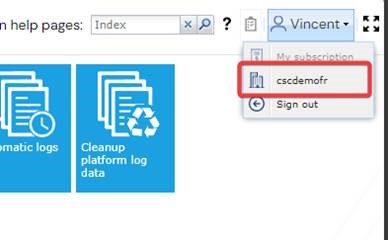
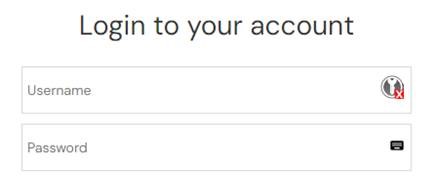
Step 1 - Authenticate to the cloud portal
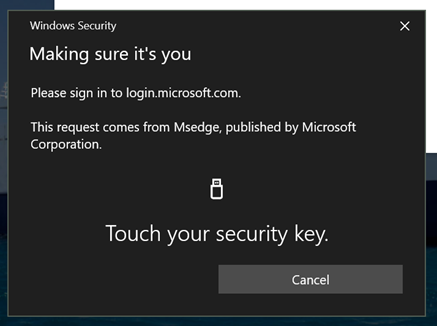
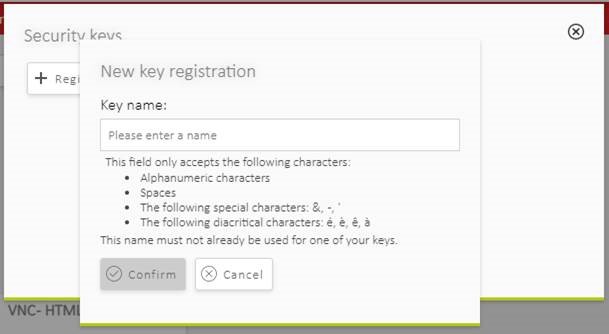
Step 2 - Register a new key
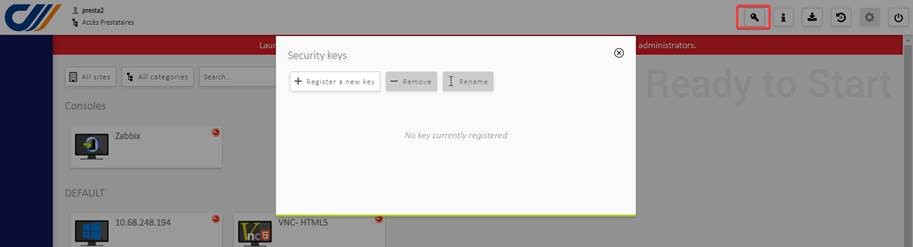
Open the key management window using the button in the top right-hand corner of the page
Click on the “Register a new key” button to start the enrollment process, and follow the steps shown in the pop-ups that follow.
Note:
This step should be completed within 30 seconds. The number of windows, their appearance and content may vary depending on various factors (OS, browser, key…)
Authentication
Once a security key has been registered to an account, that key is required to authenticate that account to the cyberelements Cloud portal for the user concerned.
If multiple keys are associated with an account, any of the keys can be used to authenticate to that account.
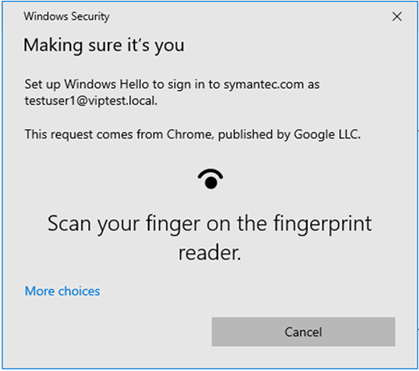
Step 2 - Insert your key
Then you will be asked to:
- Insert your key into one of your workstation’s USB ports
- If the key is already present, a PIN code will be requested (depending on the key type)
Once the steps are completed, if the security key authentication was successful, the main cloud page will be displayed. Otherwise, the login form will be displayed, and an error message will be added and traced in the access logs.
Authentication keys' Management
As an administrator of the cyberelements platform, it is possible to revoke a user’s authentication key.
Step 1 - Open the key management menu
Troubleshooting
The button for enrolling a new key for the user connected to the cyberelements web portal is only active under certain conditions.
- FIDO2 authentication is not compatible with Internet Explorer
- The user must be authenticated with a personal account to the portal and must not be authenticated via an “anonymous” domain.
- The administrator must have previously configured at least one relying party ID.
If at least one of these conditions is not met, the button is grayed out and an error message is displayed when the button is hovered. The interface consists of a list of the keys associated with the user, as well as the date these keys were added. It is also possible for the user to enroll (“Register a new key” button), unenroll or rename the key.