Happy Fool's Day!
Even though we don’t propose the Hair Analysis as a biometric authentication, Our team is working hard to make it possible in the future.
cyberelements have many other functionality to secure your organization and boost your productivity.
> Privileged Access Management
> Authentication & Zero Trust Security
> Identity Management
> Access Security Management
with cyberelements, secure all your business & privileged users and instantly give access to IT and OT systems.

The most productive access security platform on the market
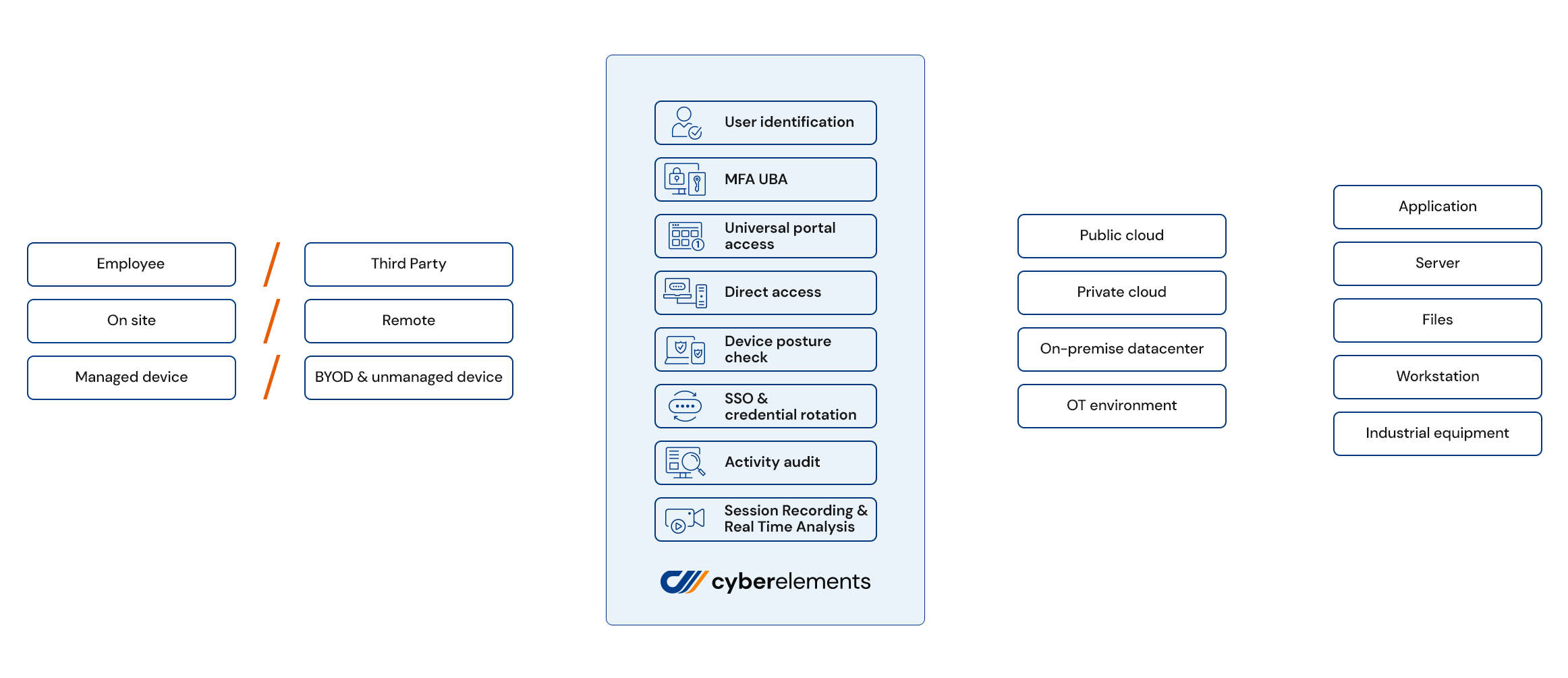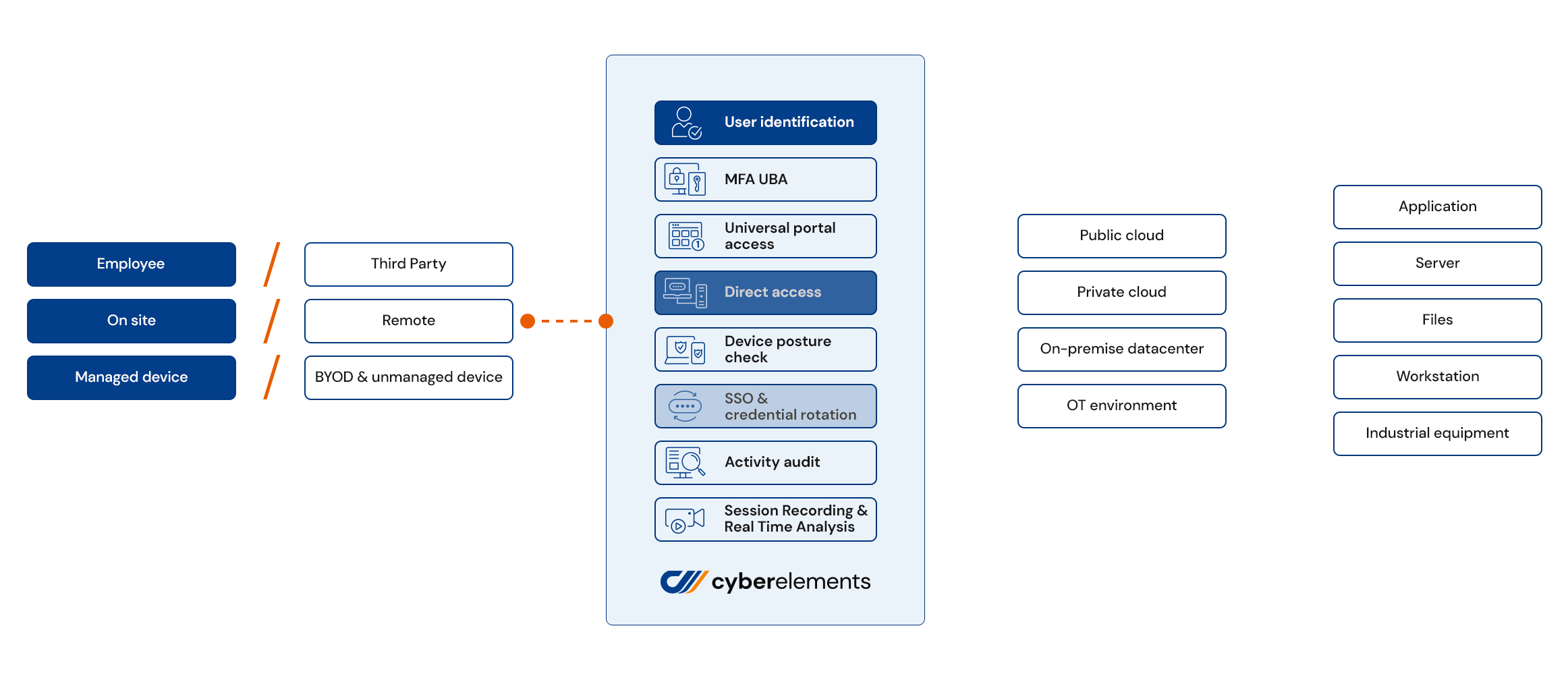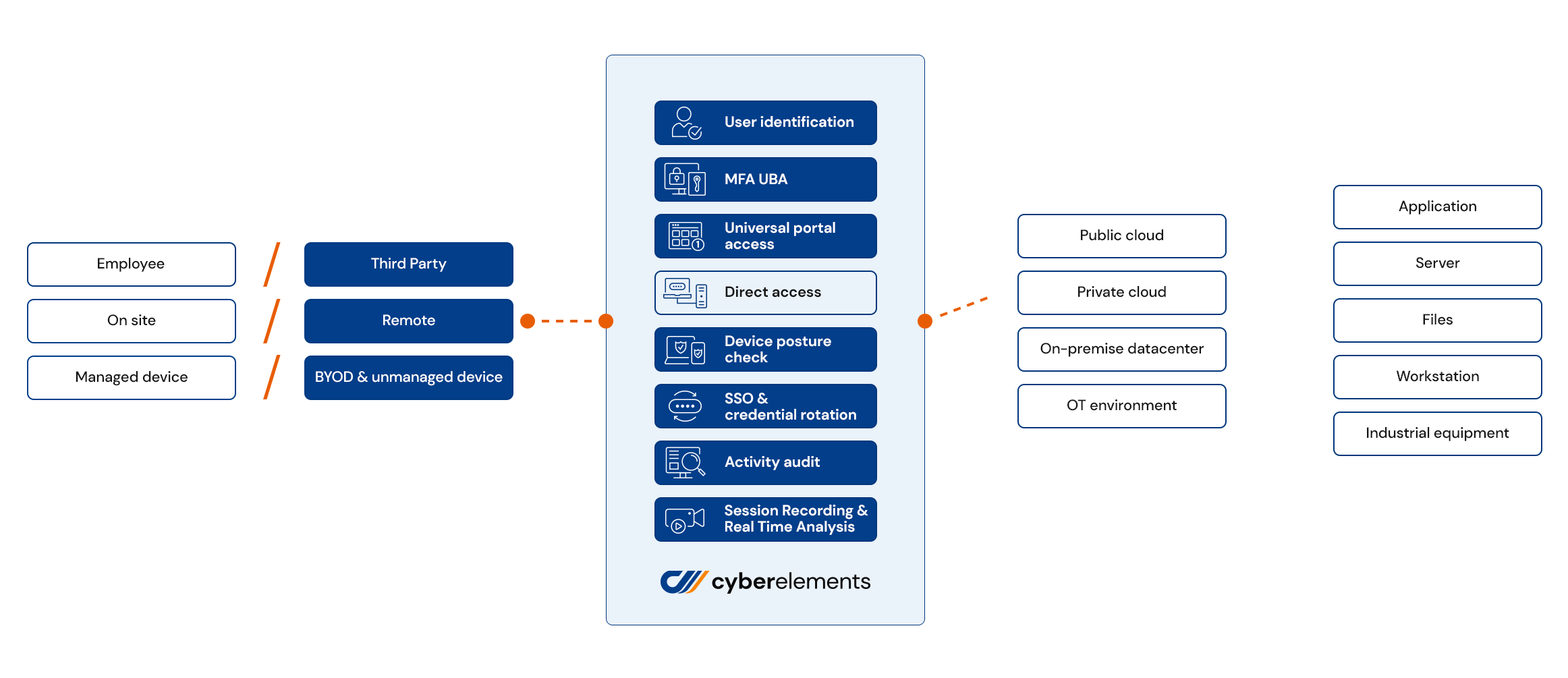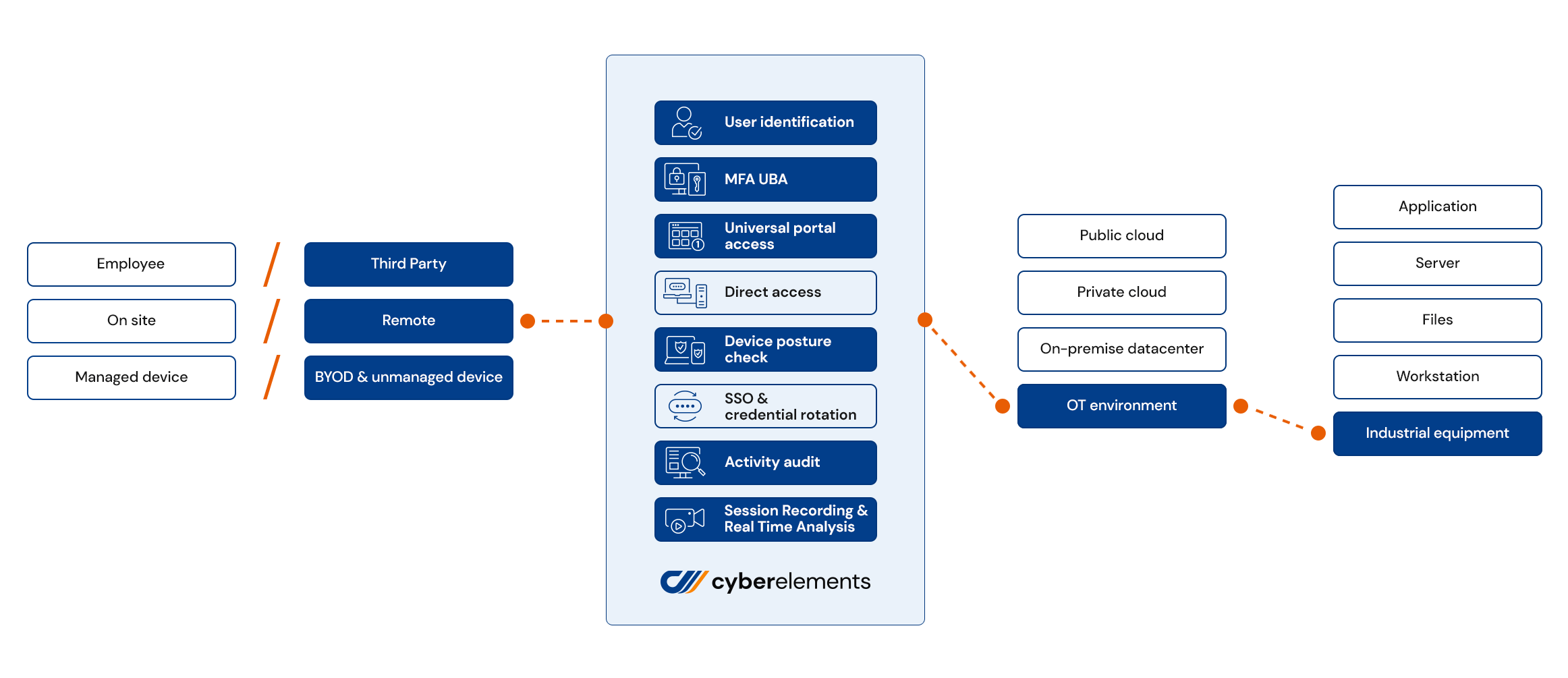
cyberelements Key Features
- Authentication & Zero Trust Security
-
Identity
Management -
Access Security
Management & Universal Portal -
Privileged Access
Management - All features

MFA
Enable Multi-Factor Authentication on both user & admin access. Connect with your existing MFA solution like Office-365, FIDO2 solutions like Yubikey, Google Authenticator, RSA & much more.

Behavioral Biometrics
Powered by Artificial Intelligence, our next-gen Continuous Authentication analyze in real-time the user behaviors when interacting with a keyboard, mouse or touch-screen and detect suspicious activities & Account Take-Over.

Device assessment
Define your own security postures and check the integrity of every device connecting to your applications & systems. Check compliance with more than 20 type of configurations such as IP, date/time, OS parameters and more.
Synchronize w/ your identities
Connect & synchronize your existing user repositories such as Microsoft Active Directory, Azure AD, OpenLDAP or any other SAML & OIDC provider.

Local users
In combination with your own user repositories, cyberelements provides a local user repository. This one can be used for creating and managing local users and cover some use-cases like third-party access.

Identity-based access policies
Define user group permissions in a way that makes sense for your corporate structure, such as by role or location. You can then create policies to determine which applications & systems groups can access, and how.

Outgoing flow w/ no port opening
Our Double-Barrier technology relies on a unique outgoing traffic flow management. Access to onPremise/Cloud applications & systems requires the deployment of an Edge Gateway that will connect to our cloud platform by a unique SSL 443-port outgoing traffic. No incoming traffic to your local network is more security!
Protocol Break
Thanks to our protocol break "in the middle", we avoid the propagation of threats (malware, ransomware, ...) between the user device and the organization's IT system.
onDemand sessions w/ random ports
cyberelements establishes the connection to a resource only at the time of use (when the user clicks on the resource icon). This ensures the maximum access security.
Easy access to every application & system
Deliver access to all your business applications & IT systems. Connect through the major protocols such as Web apps, RDP/SSH/VNC, Desktops, file shares, networks & more.

Single-Sign On
Configure Single-Sign on your apps & systems to reduce the efforts for your users to connect to their applications & systems and eliminate the need for users to manage their own credentials.
Organization Password Vault
Our password vault allows you to securely store all the corporate credentials & keys. Our session manager allows you to define the right credential you want to inject on the right session. Deployment flexibility: Vault can be deployed in the cyberelements cloud or on your premises.
Personal Password Vault
Each user can setup its own vault and store personal credentials to use with applications & systems.
Password policy & rotation management
Define and setup your corporate password policies and enforce the rotation of users & system passwords.
Password obfuscation
Our session manager allows the injection of credentials on a session/application login process and the obfuscation for the user. This allows the organization to connect users to sensitive session without disclosing credentials.
Session recording & Live streaming
Record in video every privileged session to your sensitive applications & systems. Like a CCTV system, watch in real-time all active sessions on your systems and interact with.

Session monitoring & real-time analysis
Our AI-powered engine track in real-time activities. Following your security postures, cyberelements detect and block suspicious activities.

Security policies
Define and setup your own security policies to be enforced on systems and users. Our fine-grained controls allows you track and detect actions such as process launch, commands, keystrokes, window launch, file transfers, session inactivity and more.

Advanced search
Our innovative search engine allows to search and find for specific occurred actions made on your systems. Instead of watching videos for hours or analizing tons of logs, define your request with our advanced criteria and find the right action at the right time.

Direct access
Users, specially IT admins, are likely to use day-to-day tools like session managers. Allow them to keep using their tools and connect directly to the applications & systems while still recording and tracking actions in real-time.

Just-in-Time & Workflows
Give access to your applications & systems only upon explicit demand. Thanks to our approval workflows system, users can request effective rights on applications and systems only on approval and for limited date/time/duration/number of connections.
Accounts & Assets discovery
Managing the delivery of thousand of applications & systems can be complex and time consuming. The discovery feature allows large organization to automatically discover and import assets & accounts into the cyberelements console.
app-to-app (DevOps privileged access)
Managing privileged sessions is also about managing interaction between applications or machines. Our App2App feature allows any application, script, machine to request (if allowed) our password vault to securely retrieve credentials needed to perform a specific task.
Endpoint Tunneling
The cyberelements tunneling enable local endpoints to securely and directly run any client-server application interaction while benefiting from PAM features like session recording, real-time tracking and auditing.

MFA
Enable Multi-Factor Authentication on both user & admin access. Connect with your existing MFA solution like Office-365, FIDO2 solutions like Yubikey, Google Authenticator, RSA & much more.

Behavioral Biometrics
Powered by Artificial Intelligence, our next-gen Continuous authentication analyze in real-time the user behaviors when interacting with a keyboard, mouse or touch-screen and detect suspicious activities & Account Take-Over.

Device assessment
Define your own security postures and check the integrity of every device connecting to your applications & systems. Check compliance with more than 20 type of configurations such as IP, date/time, OS parameters and more.
Synchronize w/ your identities
Connect & synchronize your existing users repositories such as Microsoft Active Directory, Azure AD, OpenLDAP or any other SAML & OIDC provider.

Local users
In combination with your own users repositories, cyberelements provides a local users repository. This one can be used for creating and managing local users and cover some use-cases like third-party access.

Identity-based access policies
Define user group permissions in a way that makes sense for your corporate structure, such as by role or location. You can then create policies to determine which applications & systems groups can access, and how.

Outgoing flow w/ no port opening
Our Double-Barrier technology relies on a unique outgoing traffic flow management. Access to onPremise/Cloud applications & systems requires the deployment of an Edge Gateway that will connect to our cloud platform by a unique SSL 443-port outgoing traffic. No incoming traffic to your local network is more security!
Protocol Break
Thanks to our protocol rupture "in the middle", we avoid the propagation of threats (malware, ransomware, ...) between the user device and the organization's IT system.
onDemand sessions w/ random ports
cyberelements establishes the connection to a resource only at the time of use (when the user clicks on the resource icon). This ensures the maximum access security.
Easy access to every application & system
Deliver access to all your business applications & IT systems. Connect tothrough the major protocols such as Web apps, RDP/SSH/VNC, Desktops, file shares, networks & more.

Single-Sign On
Configure Single-Sign on your apps & systems to reduce the efforts for your users to connect to their applications & systems and eliminate the need for users to manage their own credentials.
Organization Password Vault
Our password vault allows you to securely store all the corporate credentials & keys. Our session manager allows you to define the right credential you want to inject on the right session. Deployment flexibility: Vault can be deployed in cyberelements cloud or on your premises.
Personal Password Vault
Each user can setup its own vault and store personal credentials to use with applications & systems.
Password policy & rotation management
Define and setup your corporate password policies and enforce the rotation of users & systems passwords.
Password obfuscation
Our session manager allows the injection of credentials on a session/application login process and the obfuscation for the user. This allows the organization to connect users to sensitive session without disclosing credentials.
Session recording & Live streaming
Record in video every privileged session to your sensitive applications & systems. Like a CCTV system, watch in real-time all active sessions on your systems and interact with.

Session monitoring & real-time analysis
Our AI-powered engine tracks in real-time activities. Following your security postures, cyberelements detects and blocks suspicious activities.

Security policies
Define and setup your own security policies to be enforced on systems and users. Our fine-grained controls allows you track and detect actions such as process launch, commands, keystrokes, window launch, file transfers, session inactivity and more.

Advanced search
Our innovative search engine allows to search and find for specific occurred actions made on your systems. Instead of watching videos for hours or analizing tons of logs, define your request with our advanced criteria and find the right action at the right time.

Direct access
Users, specially IT admins, are likely to use day-to-day tools like session managers. Allow them to keep using their tools and connect directly to the applications & systems while still recording and tracking actions in real-time.

Just-in-Time & Workflows
Give access to your applications & systems only upon explicit demand. Thanks to our approval workflows system, users can request effective rights on applications and systems only on approval and for limited date/time/duration/number of connections.
Accounts & Assets discovery
Managing the delivery of thousand of applications & systems can be complex and time consuming. The discovery feature allows large organization to automatically discover and import assets & accounts into the cyberelements console.
app-to-app (DevOps privileged access)
Managing privileged sessions is also about managing interaction between applications or machines. Our App2App feature allows any application, script, machine to request (if allowed) our password vault to securely retrieve credentials needed to perform a specific task.
Endpoint Tunneling
The cyberelements tunneling enable local endpoints to securely and directly run any client-server application interaction while benefiting from PAM features like session recording, real-time tracking and auditing.
Trusted by businesses of all shapes and sizes


