Securing Remote Access to Industrial Environments
A breach of operation technology environments and cyber-physical systems can lead to catastrophic outcomes, including the potential loss of human life. In recent years, targets of OT attacks have included critical infrastructure such as nuclear plants and water treatment facilities.
Stormshield, in collaboration with L’usine digitale, produced a barometer showing the consequences of OT cyberattacks. 27% of cyberattacks led to the disruption of production. The results are shown in the graph below:
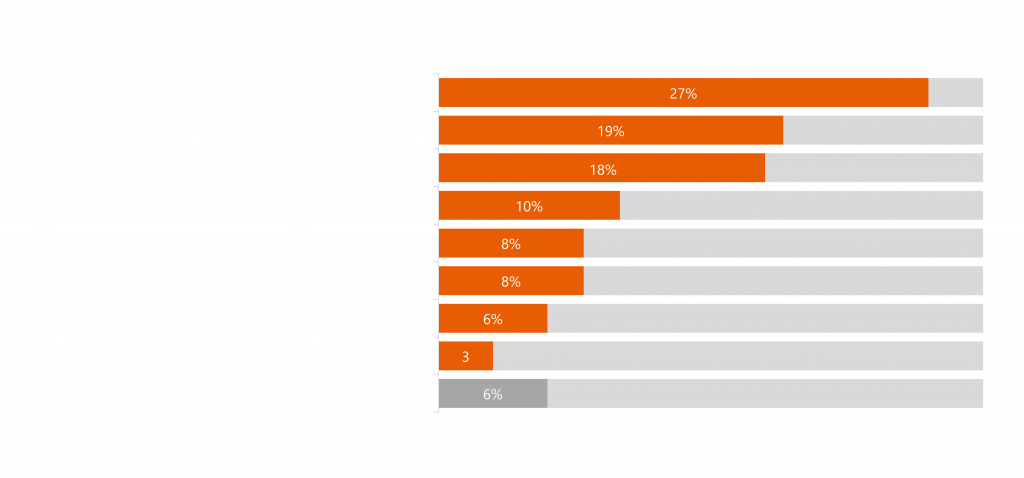
In fact, the rise of digital transformation, industrial environments are increasingly complemented by IT environments. We are now seeing substantial development in the industrial ecosystem leading to new security challenges. Therefore, creating new OT cybersecurity needs and use cases:
- Access to Industrial Control Systems (ICS): CISOs and CIO are asked to provide advanced traceability into what is exactly happening on the OT environments. They now need to give proofs showing who connected to which application/machine, did what, and at what time.
- Increasing number of remote access points: Previously workforces needed to be in front of the device to do the job. In the case of 3rd parties, they had to travel on-site to prove their identities and connect on the OT systems. Today, remote access has become a common trend forcing industries to open the doors for internal workforces and external ecosystems (vendors, manufacturers, suppliers, etc.) to connect remotely.
- IT/OT interconnection and segmentation: Industrial companies have to manage IT and OT environments while keeping a clear separation between the two.
- Leverage cloud computing: Business intelligence services provided by numerous manufacturers has required industrial companies to share collected data by sending them to the public cloud.
- File transfers: Formerly, performing an update used to be done on-site using a USB key or a hard disk. Today, files are being transferred remotely creating the need to secure these transfers from/to the external world.
In order to ensure OT environments security, we need to understand the differences between IT & OT environments first.
What are the Differences between IT & OT?
Cybersecurity presents critical challenges for both IT and OT systems, but there are fundamental differences between the two.
OT systems are generally autonomous, isolated, self-contained, and operate on proprietary software. Whereas IT systems are generally interconnected, lack of autonomy, and run on widely used operating systems (Windows and Linux).
Environments:
OT environments involve software and tools produced by various vendors and manufacturers that use proprietary protocols.
Whereas IT environments use more standard solutions and protocols such as HTTP, RDP, and SSH.
Confidentiality vs Safety:
The main goal of OT security is safety of equipment and processes. It maintains physical systems through continuous control preventing financial losses.
Whereas IT security prioritizes confidentiality, helping organizations securely store and transmit data.
Giving these differences, industrial companies need an architecture that secures both IT & OT environments taking into consideration their differences, interconnections, and interdependencies. This is why the Purdue Model provides a model that organizes the ICS infrastructure by dividing it into two zones IT & OT and subdividing these zones into seven levels.
The Purdue Model: How it secures the ICS environment?
At the core of the Purdue model is Operational Technology (OT), which includes systems located in critical infrastructure and manufacturing used to monitor and control physical equipment. At the top of the OT zone, we find the IT zone separated by a DMZ (Demilitarized Zone) ensuring access control between the OT and the IT zones.
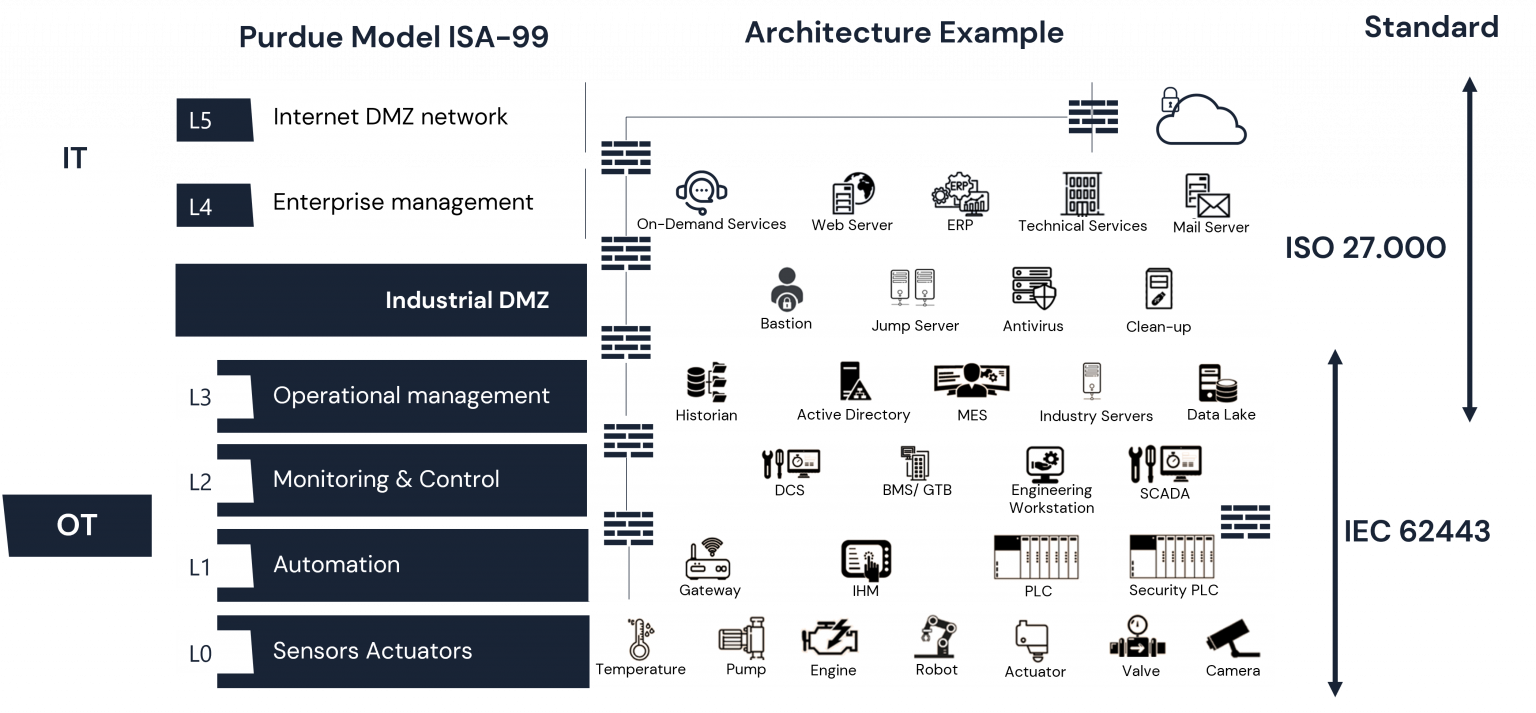
L0 – Sensors Actuators: This level includes all the hardware and physical equipment in charge of product creation.
L1 – Automation: Here we find the systems that are directly connected to the physical equipment and are used to send commands and control machines.
L2 – Monitoring & Control: Level 2 contains the devices in charge of the overall process within the process such as SCADA software and human-machine interface (HMIs).
L3 – Operational Management: This level consists of systems for managing production workflows such as data historians, batch management, and manufacturing operation management systems.
Industrial DMZ (iDMZ): acting as a barrier between the IT and the OT zones preventing any propagation of infection and blocking contamination.
L4 – Enterprise Management: Here we find systems that manage manufacturing logistics, communication, and data storage.
L5 – Internet DMZ Network: This level represents the enterprise network. Although not an ICS environment, it collects data from ICS systems to help taking business decisions.
When the Purdue model goes beyond the separation between IT and OT environments, it allows granular segmentation of the two through a layered architecture. An industrial environment will still need to secure and properly manage access to these different layers. Critical access is best secured using a PAM solution (Privileged Access Management solution).
At cyberelements, we provide a PAM solution that can seamlessly integrate an infrastructure that is based on the Purdue Model.
How Can The cyberelements PAM Solution Fit To The Purdue Model Infrastructure?
The double barrier architecture of cyberelements is designed for this type of infrastructure. Having two components: The Controller and The Edge Gateway securely connects users only to the resources needed to perform a task.
The Edge Gateway:
To keep the separation among the different levels, cyberelements provides a gateway per level. At each level, we will have an Edge Gateway that is connected to The Controller. You can go further with cyberbelerments by separating several (V)LANs if applicable. This will not impact the end user experience: the OT operator will see all the OT resources within a single “pane of glass”.
The Controller:
In The Controller we have two separate tenants: one for the IT zone and one for the OT zone. This organization will connect IT workforces to the IT zone and the OT workforces to the OT zone.
This unique architecture makes sure that we are running on outgoing traffic flow:
The user requests the access at The Controller level and the relevant Edge Gateway will establish the connection and send the session to The Controller and then to the user.
How Does cyberelements Respond to Emerging Use Cases?
- Giving secure remote access to an engineering workstation hosting an ICS application
When the engineering workstation is located in the OT environment, the job of cyberelements is to give secure access to the workstation for all type of users (external service providers, manufacturers, employees, etc.). The user, after being authenticated with MFA (Multi-Factor Authentication), will connect to The Controller that will run a device conformity check and grant access to previously approved resources. Thanks to the password vault, all passwords are securely stored and automatically injected to avoid credential disclosure and to enhance user experience.
cyberelements allows you to record the sessions, track what is being performed, and to set up automatic detection of suspicious behaviors.
- Remote use of the manufacturer’s application via the bastion
Users are using their own endpoint where the tools are installed. The cyberelements platform here will connect these tools to the OT equipment, establishing an on-demand secure connection per protocol and per application through a secure tunnel connecting from the endpoint to the relevant equipment. Thanks to the use of a generic tunnel, cyberelements covers all type of protocols and all type of applications.
- File Transfer Security
File transfer is needed to perform many operations on the OT environment. However, files need to be verified before transferring them into the internal zone. cyberelements plays a vital role to secure file transfer by adding an extra security check before any file can access the internal OT environment. Let’s take the example of a third party that needs to connect to an OT equipment to perform an update. The admin will have to upload the file to the cyberelements exchange zone that is isolated from the rest of the OT environment. The diode network will check the file if it is safe before transferring it to the internal data exchange zone.
HTML5 for Enhanced User Experience and Advanced Security
With cyberelements external users can securely connect through a web browser without the need of installing any agent. The resources will be displayed in the cyberelements platform limiting the risk of threats propagation.
In fact, the protocol break in The Controller ensures that there is no direct connection between the endpoint and the OT environment. It is, therefore, breaking down the protocols by using HTML5 between the endpoint and The Controller and technical business protocol between The Controller and the OT environment.
At cyberelements we have helped numerous customers from the industrial sector securing remote access to OT environments. If you would like to learn more about our platform, our team will be more than happy to demonstrate the solution’s capabilities: Book a meeting now
Or start now for free, it takes 3 mins to enable your platform: Start now