Use Cases
Break-up with multiple complex security tools and understand how cyberelements can help you unify & simplify your access security control for all use-cases
Enable workforces to access from anywhere
cyberelements enables remote workforces to securely access to their working environment, whether in mobility or on a « work from home » context
The same remote access solution applies as well for third party organization access.
Whether from a corporate owned device or from a personal (BYOD) device, cyberelements turns untrust into trust, by applying the « Zero-Trust » paradigm to remote access.
The first productivity requirement for a remote employee is to rapidly and securely access to the organization’s IT systems: get rid of the VPN risk and scalability issues; avoid credential disclosure or exposure; even avoid IT system exposure on the Internet.
Zero-Trust Network Access made simple & effective
Full-Isolation: device-IT system & IT system/Internet
![]() Context-aware access (conformity check)
Context-aware access (conformity check)
Control and monitor privileged users
cyberelements natively enables remote privileged access to the most critical IT assets: computing servers, storage servers, network devices, applications, data infrastructure
cyberelements natively enables remote privileged access to the most critical IT assets: computing servers, storage servers, network devices, applications, data infrastructure. Whether for the organization’s own employees or for third party contractors. Via any protocol to any resource (Web, RDP, SSH).
Amongst the main security threats, RDP compromission and VPN vulnerability are at the top of the list. This is why cyberelements natively implements a « Zero-Trust » security policy.
In addition, with cyberelements, no customer data ever leaves the organization’s own sensitive environment, and the data flow in and out of the organization’s network is encrypted with an organization’s own key: there’s no risk of exposure – either accidental or malicious.
 Multifactor authentication (MFA) & SSO
Multifactor authentication (MFA) & SSO
![]() Session audit trail, recording and real-time analysis
Session audit trail, recording and real-time analysis
 Password vault and rotation policies
Password vault and rotation policies
Secure 3rd parties & MSP access
Hackers try to leverage the doors opened to third party organizations in order to penetrate an organization’s network.
Learn how cyberelements helps you to stay away from “Supply Chain Attacks”
From a cybersecurity viewpoint, you cannot trust a third-party device or employee. If there is a place where the “Zero-Trust” principle must apply, it is here.
A key challenge with third party access is that you often need to grant access in minutes when it was not planned: cyberelements is the most rapid and secure way to give customers, suppliers, partners access to the organization’s IT system.
The security bar will be adjusted according to the security risk: multifactor authentication; session recording; device check; etc.
 Access policy level according to the security risk
Access policy level according to the security risk
 No service exposed; no credential disclosed
No service exposed; no credential disclosed
 Agentless deployment; intuitive web portal experience
Agentless deployment; intuitive web portal experience
Manage OT Operators
Remote access to OT systems remains a challenge. What if you had a single solution for both IT and OT access, for both internal and external access?
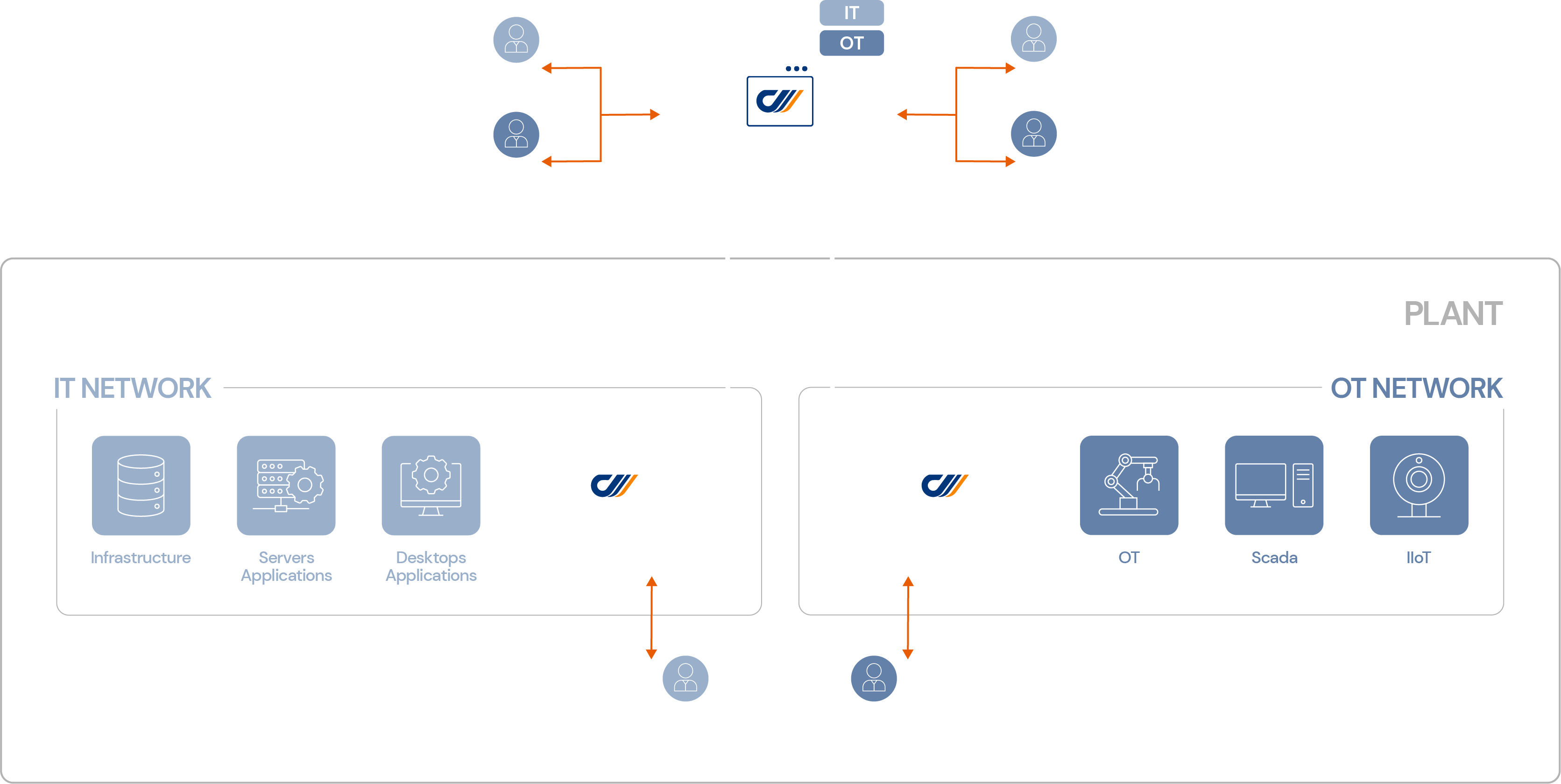
Access to IT systems and OT systems are often privileged and performed with a bunch of scattered solutions.
Remote access to OT systems remains a challenge. What if you had a single solution for both IT and OT access, for both internal (from within the network) and external (from the Internet) access ?
cyberelements is the only Zero-Trust solution which allows to segment and isolate all these access contexts within the same product and a single user experience.
With cyberelements, no customer data ever leaves the organization’s own sensitive environment, and the data flow in and out of the organization’s network is encrypted with an organization’s own key: hence, there’s no risk of exposure – either accidental or malicious.
 Secure access without any inbound opening – only outgoing flows
Secure access without any inbound opening – only outgoing flows
 No service exposed; no credential disclosed
No service exposed; no credential disclosed
 Complete isolation between IT and OT, internal and external
Complete isolation between IT and OT, internal and external
Trusted by businesses of all shapes and sizes


