What is Native Zero Trust Remote PAM?
By the year 2026, organizations embracing least privilege approaches to RPAM use cases are projected to significantly reduce their risk exposure, by more than 50%.
Gartner
Native Zero Trust remote PAM: What is it & what are the benefits?
For privileged users connecting remotely, native Zero Trust PAM is designed to manage privileged access by applying Zero Trust principles. It allows organizations to enforce the principle of least privilege access by operating under the assumption that all privileged users and devices pose potential security threats. The connection between end users’ devices and the organization’s systems is highly secured by features such as URL rewriting technology, random ports generation, restricting the connection to the period or the conditions of use. Zero Trust remote PAM also allows organizations to implement contextual and dynamic security controls. These controls identify potential threats and malicious user activities in real time and promptly revoke access or trigger automated responses.
Why do we need remote PAM?
On one hand, organizations’ ecosystems are expanding, increasing the number of third-party service providers which need to access the organization’s IT or OT systems. On the other hand, remote working has increased since the COVID pandemic. Creating the urge to secure remote access for privileged users. Therefore, Remote PAM emerges as a critical solution to fortify their security posture, mitigate risks and uphold the integrity of their IT & OT systems.
Remote PAM has a wide range of use cases:
Organization’ s IT administrators
External IT or OT service providers
Operational technology (OT) maintenance and help desk users
Connecting remotely to critical IT or OT systems.
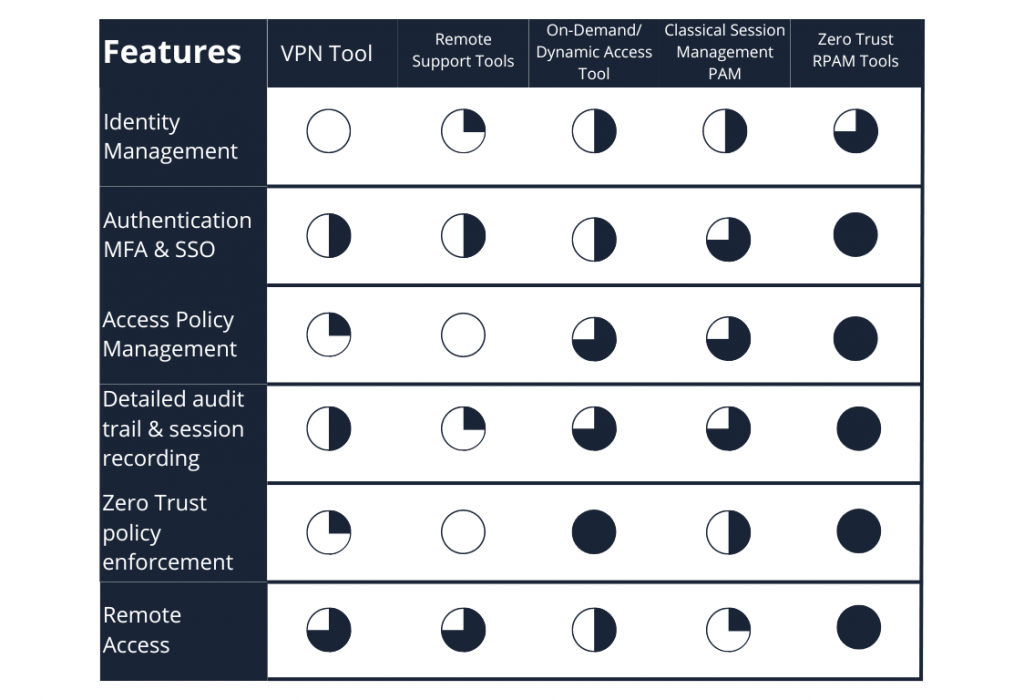
VPN vs Remote PAM
The organizations’ security needs are evolving due to a change in the corporate network scope: we cannot consider the corporate network as the “security perimeter” anymore. The paradigm is no more: “inside safe, outside danger”. Hence the shift in the way to approach remote access use cases. The security perimeter has changed. And the technologies which were designed for the network as the security perimeter, such as the VPN technology, may become a risk in this new landscape.
That is why Zero Trust Network Access (ZTNA) technologies have emerged and are being used increasingly. The table below summarizes the differences between VPN and ZTNA.
What is Zero Trust?
Conventional Privileged Access Management provides basic features that are not enough to secure remote privileged access anymore. A Zero Trust approach should be adopted in this context.
However, what is Zero Trust about? Is it a marketing buzz?
Zero Trust is a security framework that requires ongoing verification and authorization for all users attempting to access enterprise resources, thereby preventing unauthorized access. This approach ensures that users and devices are never trusted, even when connected to the organization’s network. By adopting the “never trust, always verify” approach, organizations can swiftly detect and block malicious activities in real time, a capability often lacking in traditional perimeter-based security strategies.
In traditional approaches, users and devices are granted static access to IT resources within the network perimeter. Consequently, if an attacker infiltrates the organization’s network, they can freely navigate within it and compromise critical resources and data. This highlights the significance of Zero Trust in modern organizations.
Zero Trust is a comprehensive strategy designed to be implemented across the entire infrastructure. It allows administrators to impose additional restrictions on select critical systems and accounts, shielding them from both internal and external threats and minimizing the risk of data breaches.
The effectiveness of Zero Trust has made it become a widely popular topic in cybersecurity. It is definitely not just a marketing buzz but a basis of modern access security, innovating the way we do cybersecurity.
Native zero-trust RPAM tools offer then several benefits:
- They enable least privilege principles, effectively blocking lateral movement and reducing the risk of infected endpoints.
- RPAM tools allow for time-bound, session-specific, just-in-time access.
- They facilitate privileged access management for external users.
- RPAM tools also enable a VPN-less approach, enhancing flexibility and security.
What to consider when searching for a RPAM tool?
- Considering the identity of people ensures that access privileges are aligned with individual roles and responsibilities, thereby reducing the risk of unauthorized access.
- Evaluating the identity of assets helps organizations prioritize protection measures based on the criticality and sensitivity of the resources, enhancing overall security posture.
- Addressing the identity of processes involves understanding the workflows and procedures through which access is granted, ensuring compliance and accountability.
- Defining access entails establishing clear criteria and policies governing who can access what resources under what circumstances, fostering transparency and control over privileged access.
The cyberelements RPAM key features
cyberelements.io is the security platform for business performance, designed to seamlessly secure remote privileged access. It is a single platform for all your organization’s use cases.
Security by design: Zero Trust Access Infrastructure
The platform is built on a Zero Trust access infrastructure, characterized by a fundamental shift from the traditional perimeter-based security model, emphasizing continuous verification of user identity and device trust before granting access to resources.
Thanks to its double barrier architecture, this infrastructure ensures that no application or resource is exposed to the network by default, reducing the attack surface and mitigating the risk of unauthorized access or data breaches.
By implementing random and volatile ports, along with protocol breaks and dynamic posture checks, zero trust access infrastructure provides a resilient security framework that adapts to evolving threats and user behavior, ensuring a secure and scalable access control mechanism.
Built-in Zero Trust:
- Zero Trust RPAM solution incorporates continuous and dynamic posture checks, ensuring that access is granted based on the real-time security status of the user’s device.
- It also conducts continuous and dynamic behavior and context checks of end-users and their devices, allowing us to adapt access privileges instantly based on user activity and potential risks.
- With Zero Trust by design, it guarantees that no application or resource is exposed to the network by default, protecting critical resources against brute force attacks or access attempts, thanks to, for example, only outgoing flows (no port opening) and URL rewriting on the server side. This enforces the access to an IT or OT resource to go through the RPAM product.
- Random and volatile ports, enhancing security by minimizing predictability and making it more difficult for potential attackers to exploit vulnerabilities.
- Protocol breaks, disrupting conventional attack methods and bolstering our security defences, ensuring a more resilient infrastructure against emerging threats.
- Leveraging isolation technology, our solution restricts access to only image display and mouse/keyboard flow, minimizing the attack surface and providing a highly secure environment for privileged access.
- Less resource-consuming scalability, ensuring optimal performance and cost-effectiveness while maintaining robust security measures, suitable for organizations of varying sizes and resource constraints.
Key Functionalities:
- Session recording and auditing capabilities, allowing organizations to maintain detailed logs of all privileged access activities for compliance, forensic analysis, and security incident response purposes. The video recordings can sit in your premises or in the cloud, depending on your preferences.
- Advanced search providing visibility into privileged sessions and tracking possibility of user activities. It allows you to identify potential security breaches or policy violations, thereby enhancing governance, risk management, and overall security posture. Making thus a detailed forensic analysis much easier.
- Double barrier architecture with a mediation controller and edge gateways, as a secure entry point for privileged users, enforcing strong authentication and access controls to ensure that only authorized individuals gain entry to critical resources.
- Robust authorization mechanisms, enabling organizations to enforce least privilege principles, granting users only the access they need for their specific tasks or roles, thereby reducing the risk of unauthorized access and potential security breaches.
- Just-in-time access feature, dynamically provisioning access privileges on a per-session basis, granting temporary and time-bound access only when needed, minimizing the exposure window and enhancing security posture by limiting the opportunity for exploitation or misuse.
- Robust local identity store, enabling organizations to securely manage and authenticate privileged user accounts within their internal systems, enhancing control and visibility over access permissions and user credentials.
- Identity federation, extending access management beyond organizational boundaries, allowing seamless integration with external identity providers and enabling federated authentication, simplifying access for users while maintaining security standards.
- Advanced session management, our RPAM solution provides administrators with granular control over privileged sessions, allowing them to monitor, terminate, or even record sessions in real-time, enhancing accountability and auditability while ensuring compliance with security policies.
- Password vaulting and credential injection, allowing organizations to securely store and manage privileged credentials, eliminating the need for users to manually enter passwords and reducing the risk of credential theft or misuse, thereby enhancing security posture and operational efficiency.
- Multi-Factor Authentication (MFA) and Single Sign-On (SSO), adding an additional layer of security to privileged access, requiring users to provide multiple forms of verification, or enabling seamless access to multiple resources with a single set of credentials, enhancing security while improving user experience and productivity.
At the end, it is important to mention that security is not about creating walls. It’s about giving the right people the right access to the right resources at the right time, in a secure and compliant manner. This is why at cyberelements our mission is to provide organizations a converged secure platform to manage access and comply. Your RPAM solution is deployable in 3 mins, can easily be scaled up, and delivers an intuitive user experience.