Why Zero Trust security has become a must-have for every organization?
Zero Trust security is rapidly becoming a central pillar of modern cybersecurity strategies. This year’s InCyber conference focused entirely on the theme of Zero Trust, ANSSI is preparing publications on the topic, and every vendor now brings their own definition, approach, and solutions.
Navigating all of this can be challenging, especially since Zero Trust security isn’t a formal standard: it’s a paradigm, a way of thinking. That means everyone can be right or wrong.
Systancia, recognized multiple times by Gartner as the only European vendor with true Zero Trust technology, has provided a strong and mature response for years, particularly in securing remote access, privileged access management (PAM), and identity and access management (IAM). As new digital perimeters increasingly rely on the Cloud and the need for rapid deployment, Systancia, through cyberelements, has introduced the first and only SaaS platform built entirely on the Zero Trust model.
Grounded in the state-of-the-art guidance defined by the National Institute of Standards and Technology (NIST), we demonstrate how Systancia delivers a relevant, rigorous, and rational Zero Trust approach.
NIST offers a clear definition: « La confiance “Zero Trust is a cybersecurity paradigm focused on resource protection and the premise that trust is never granted implicitly but must be continually evaluated.”
The need to dynamically manage identities
Zero Trust is, above all, a security policy. The NIST (National Institute of Standards and Technology) defines it clearly: “These protections usually involve minimizing access to resources […] to only those subjects and assets identified as needing access”.
Traditionally, VPNs which are network-to-network connections addressed security at the perimeter level: you grant access to an entire set of resources. The main consequence? Lateral movement by attackers, leading to potentially irreversible damage.
A true Zero Trust approach requires that no one has default access to applications (resources, servers, workstations, infrastructure, any digital service) and that each user only has access rights to the specific resources they need. This is described using terms like: least privilege; JIT privilege zero standing privilege.
NIST places strong emphasis on this need for granularity: “making the access control enforcement as granular as possible“.
Given the sheer volume of applications, data, and other resources that need to be controlled, it is unrealistic to manage access manually.
This is where an Identity Governance and Administration (IGA) solution like cyberelements Identity comes in. It provisions and de-provisions users, accounts, and access rights across directories and applications, using workflow mechanisms that ensure decisions are routed to the appropriate user.
One of the key aspects of the Zero Trust concept is dynamic security management. NIST clarifies this point: “All resource authentication and authorization are dynamic and strictly enforced before access is allowed.“.
This means that authentication occurs at the time of access and must be subject to strict controls. Clearly, this includes Multi-Factor Authentication (MFA) ideally just before access to a resource using the best available MFA technology to minimize user friction. It also involves real-time compliance checks: if something in the environment changes, access can be revoked instantly. NIST puts it this way: “Access to resources is determined by dynamic policy — including the observable state of the client identity, application/service, and requesting asset — and may include other behavioral and environmental attributes.“.
Authorization, then, must be handled through an identity management solution. At a minimum, access to a resource is time-bound. For example, your service provider may only have access to your RDP server or Oracle database at a specific time and date. At the highest level, you implement ephemeral identities or accounts that exist only for the duration of a specific task.
Systancia supports both approaches. It’s not just an IGA product, and it’s more than a secure remote access solution with dynamic compliance checks. It’s the combination of both that makes the cyberelements SaaS platform so powerful. It enables organizations to fully enforce the Zero Trust security in a seamless and efficient way.
Securing resources from the infrastructure up
NIST takes a radical approach that requires a completely new way of thinking about security: “Zero trust security models assume that an attacker is present in the environment and that an enterprise-owned environment is no different—or no more trustworthy—than any nonenterprise-owned environment.“.
It’s not just about access policies, it’s primarily about access infrastructure being capable of stopping attacks. This requires a combination of innovative and clever technologies designed to make attacks ineffective.
Architecture is the critical component. Systancia’s design choice is clear: a user connecting from outside the organization should never require opening a port from the outside in. Instead, a gateway within the network initiates a connection to a secure control server, which then enables the session.
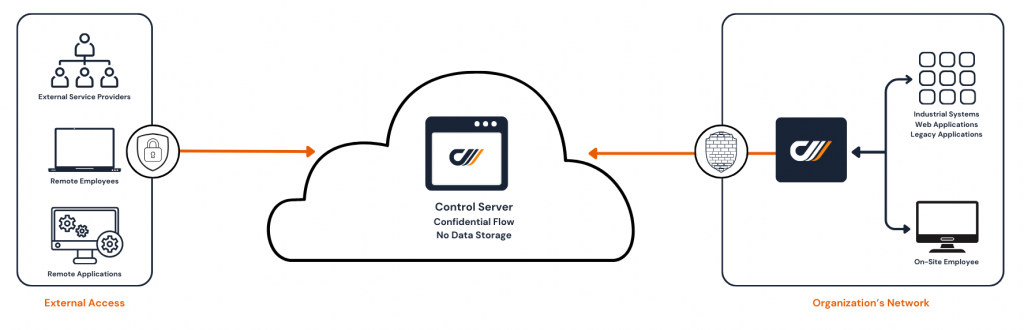
The double-barrier architecture provides strong security, especially since the control server holds no data or identity information. It acts as a secure transit gateway. This setup is reinforced with protocol break techniques, using HTML5 filtering, where access is granted via a browser that only allows keyboard and mouse interactions. The user’s workstation has no direct access to the network they are entering. It is fully aligned with the NIST approach, which assumes an attacker may already be present.
It’s also essential to segment access using solutions that maintain ease of use. If your internal networks are clearly separated (e.g., IT vs. OT, AD Tiering, etc.), the access solution should not reconnect what you’ve intentionally isolated and thus introduce new risk. cyberelements enables this through a fully multi-tenant approach for both organizations and networks, recreating strict separation for access, without placing excessive constraints on users.
cyberelements, the only SaaS platform built natively on Zero Trust
Systancia has made significant investments to deliver the best in Zero Trust security, with a core architecture certified and initially qualified by ANSSI as early as 2016.
Every key element that objectively defines Zero Trust, as laid out by NIST, is fully embedded within the cyberelements platform.