Zero Trust Lines of Defense
Mapping the NIST Zero Trust Architecture Report
“Trust is a vulnerability that cyber threats exploit. Zero Trust is how we close the gap.”
This idea has never been more relevant in today’s digital-first world. With 63% of organizations globally claiming to implement a Zero Trust model, it’s clear this approach has become a foundation of modern cybersecurity. Yet, many still grapple with understanding its principles and applying them effectively. So, what does Zero Trust really mean, and how can it transform the way we approach cybersecurity?
The Foundation of Zero Trust
Zero Trust flips the traditional security mindset on its head. Instead of assuming trust, it enforces a “never trust, always verify” approach. The NIST 800-207 framework defines seven core tenets of Zero Trust Architecture to guide its implementation:
- All data sources and computing services are considered resources.
- All communication is secured regardless of network location.
- Access to individual resources is granted on a per-session basis.
- Access is determined by dynamic policy, informed by identity, application, and behavioral or environmental attributes.
- The enterprise collects as much information as possible about the state of assets, networks, and communications to improve its security posture.
- Continuous monitoring ensures the integrity and security posture of all owned and associated assets.
- All resource authentication and authorization are dynamic and strictly enforced before access is allowed.
These principles provide a strong foundation for securing modern IT environments.
NIST also identifies critical assumptions for Zero Trust, highlighting the need to rethink network security:
- The enterprise private network is no longer considered an implicit trust zone.
- Devices on the network may not be owned or configurable by the enterprise.
- No resource, whether user or system, is inherently trusted.
- Not all enterprise resources reside on enterprise-owned infrastructure.
- Remote users and devices cannot fully trust their local network connections.
- Security policies must remain consistent across enterprise and non-enterprise environments, regardless of location.
These assumptions reflect the reality of modern, distributed IT environments and emphasize the need for a comprehensive and adaptive security strategy.
Why Zero Trust Matters?
Traditional networks relied on trust zones, assuming everything inside the network was safe. But with remote work, BYOD policies, and cloud adoption, this approach no longer works. Zero Trust recognizes that:
- Devices on your network may not be secure or managed by your organization.
- Local network connections can’t be trusted implicitly.
- Security policies must adapt seamlessly across on-premises, cloud, and hybrid environments.
Real-World Use Cases
Zero Trust isn’t just theoretical—it solves real problems in modern IT:
- Remote Access: Protecting employees working across cloud platforms, multi-site offices, or personal devices.
- Privileged Access Management (PAM): Securing sensitive accounts and limiting the impact of breaches.
- Third-Party Access: Safeguarding connections with vendors, contractors, and Managed Service Providers (MSPs).
ZTNA vs. VPNs: A More Secure Way to Connect
VPNs, once the gold standard, now struggle to meet modern security needs. Zero Trust Network Access (ZTNA) offers clear advantages:
- Clientless access: Ability to access critical resources from just a web browser, with protocol break.
- ’Single pane of glass’ access to many clouds and datacenters: A single UX to access resources in multiple sites.
- Infrastructure cost: Much lower computing resource consumption and better scalability.
How cyberelements Maps to the NIST Tenets
Core Tenets and cyberelements’ Response
The NIST 800-207 tenets provide a framework for Zero Trust architecture. Let’s take a look at the first 3 tenets:
- All data sources and computing services are considered resources.
- All communication is secured regardless of network location.
- Access to individual resources is granted on a per-session basis.
cyberelements addresses these core tenets with precision and innovation thanks to its unique architecture:
Double barrier architecture based on two components: The Mediation Controller and The Edge Gateway. The Controller is based in the cloud, operated by cyberelements and Gateways are located in your organization’s sites. The Gateway connects to the Controller and establishes an outbound tunnel. The user connects to the Controller via a secure tunnel. When the user needs to access a resource, the connection to the resource is established only at the time of the resource access, through the established tunnels. Resources are not exposed to the Internet: cyberelements generates random and volatile ports on the frontend side, and rewrites all application urls on the backend side.
With cyberelements:
- All data and services are treated as resources:
Users perform their jobs by accessing to the cyberelements portal where only resource images are displayed. The user can only send back mouse/keyboard flows.
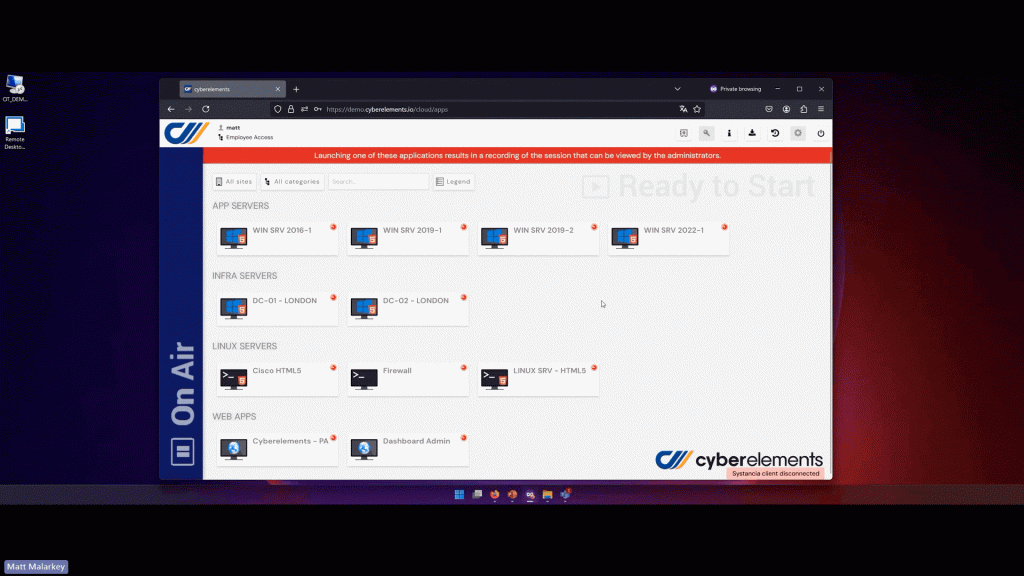
- Communication is secured regardless of location:
Using protocol isolation and secure tunneling, cyberelements ensures that all communication remains protected, whether inside or outside the organization. - Per-session access is enforced:
cyberelements enables just-in-time (JIT) access, dynamically authenticating each session based on user identity, device posture, and contextual factors.
Advanced Tenets and cyberelements’ Approach
The last NIST tenets emphasize dynamic authentication and improving security posture through real-time data:
- Access is determined by dynamic policy, informed by identity, application, and behavioral or environmental attributes.
- The enterprise collects as much information as possible about the state of assets, networks, and communications to improve its security posture.
- Continuous monitoring ensures the integrity and security posture of all owned and associated assets.
- All resource authentication and authorization are dynamic and strictly enforced before access is allowed.
cyberelements responds to these requirements with the following capabilities:
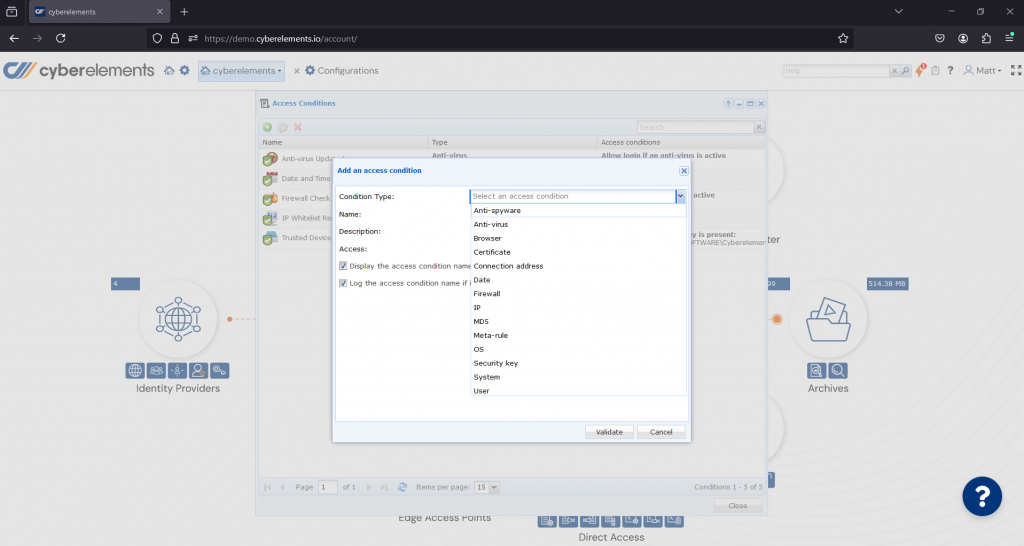
- Dynamic access policies including authentication and authorization:
cyberelements enforces multi-factor authentication (MFA) and behavioral analysis to ensure every access request is validated dynamically. with fine-grained access controls, ensuring that nothing is inherently trusted.
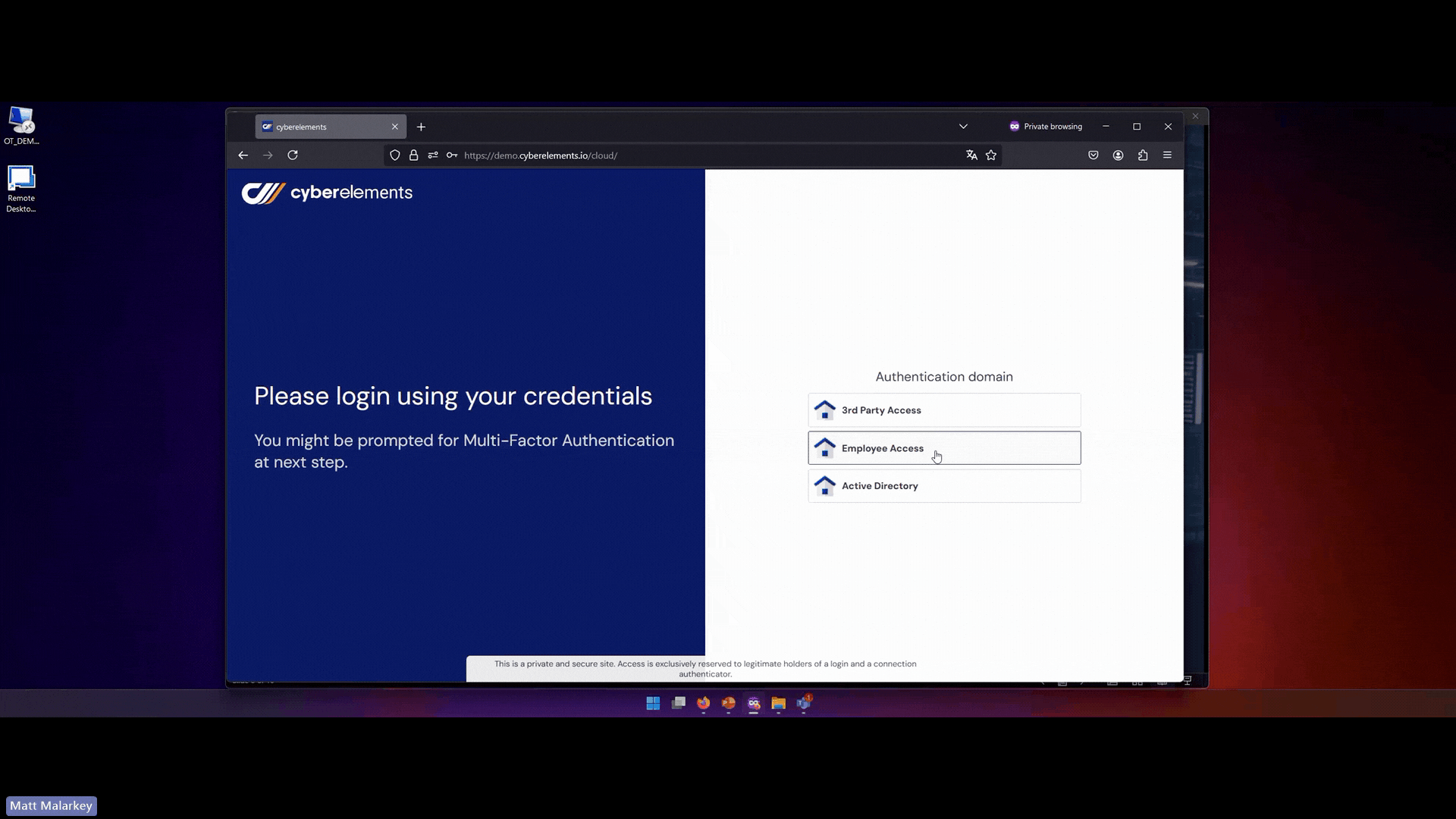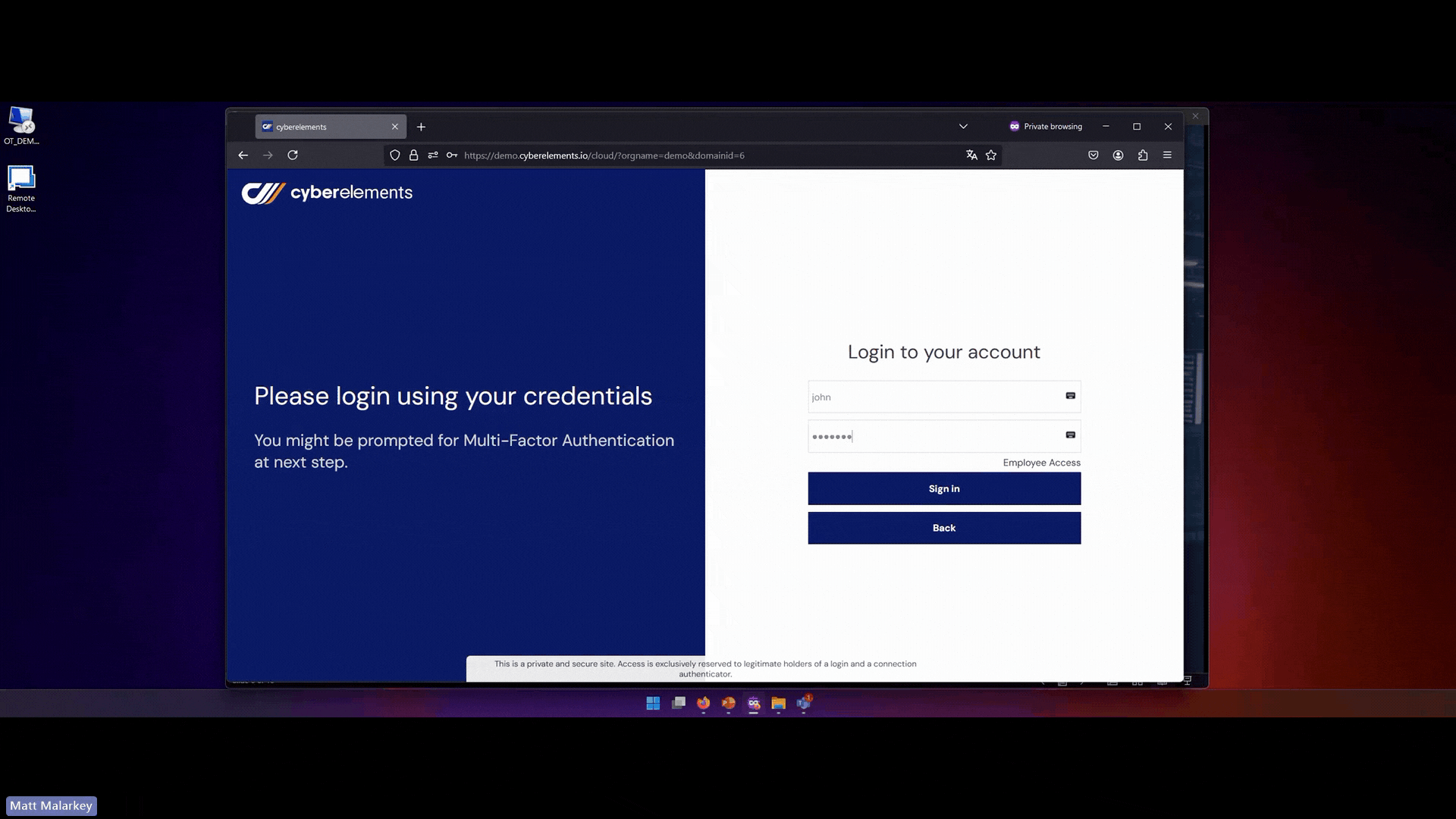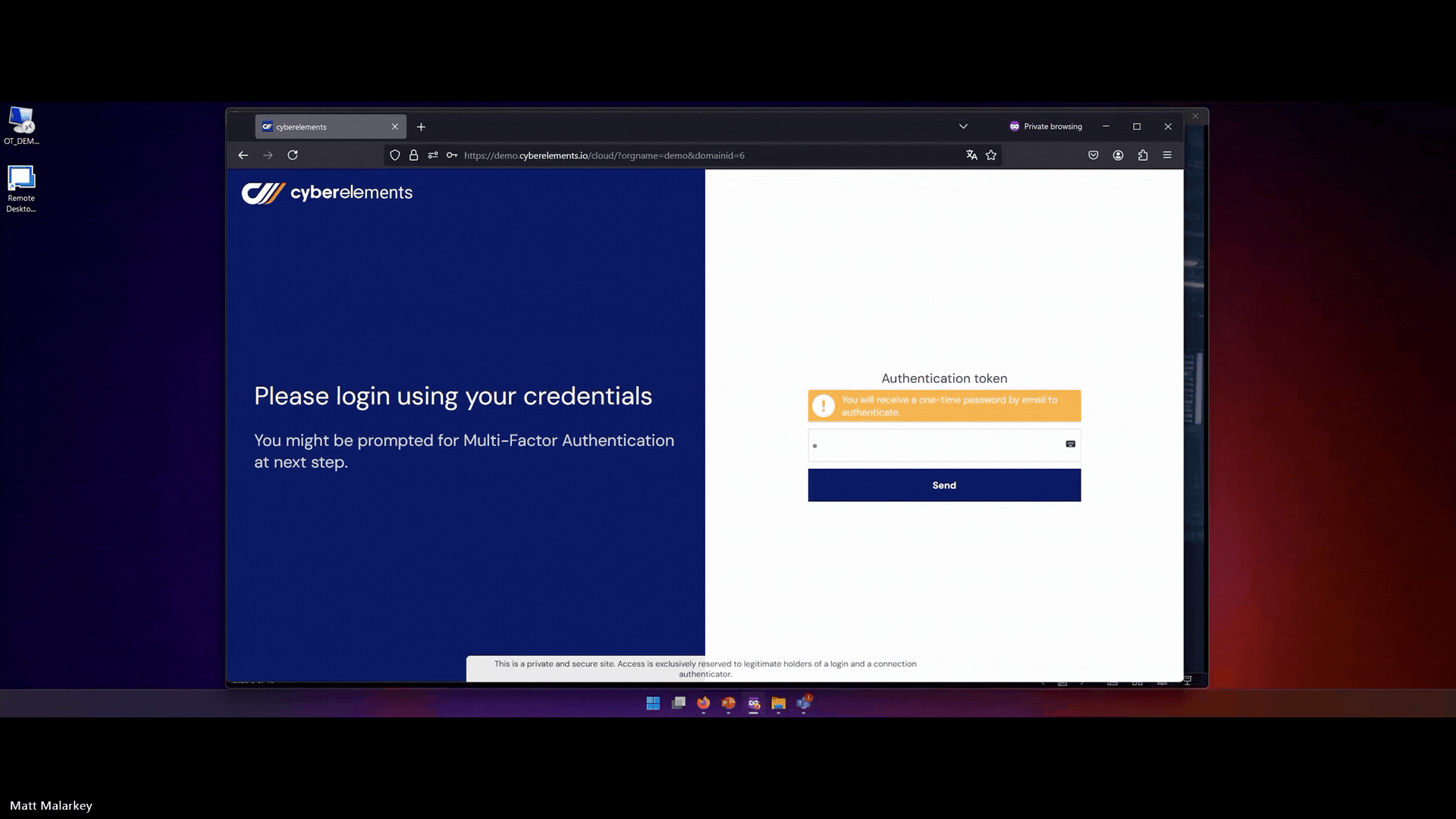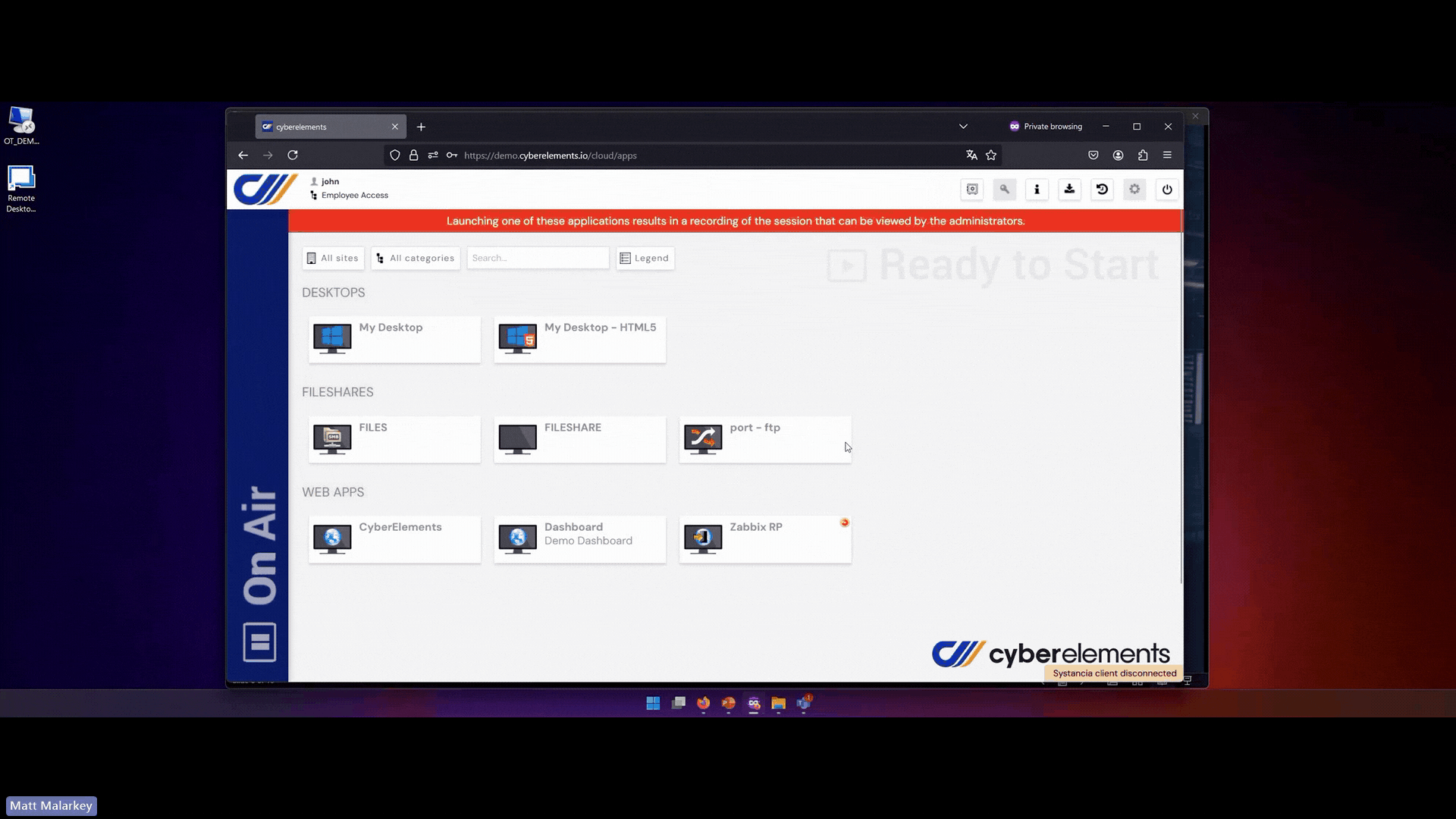
- Integrity monitoring for users, devices, and networks:
cyberelements continuously evaluates the state of connected devices, user behavior, and network conditions to maintain a high-security posture.
- Continuous monitoring and refinement of defenses:
Real-time analytics and monitoring tools within cyberelements provide continuous insights, allowing organizations to detect and address vulnerabilities proactively.
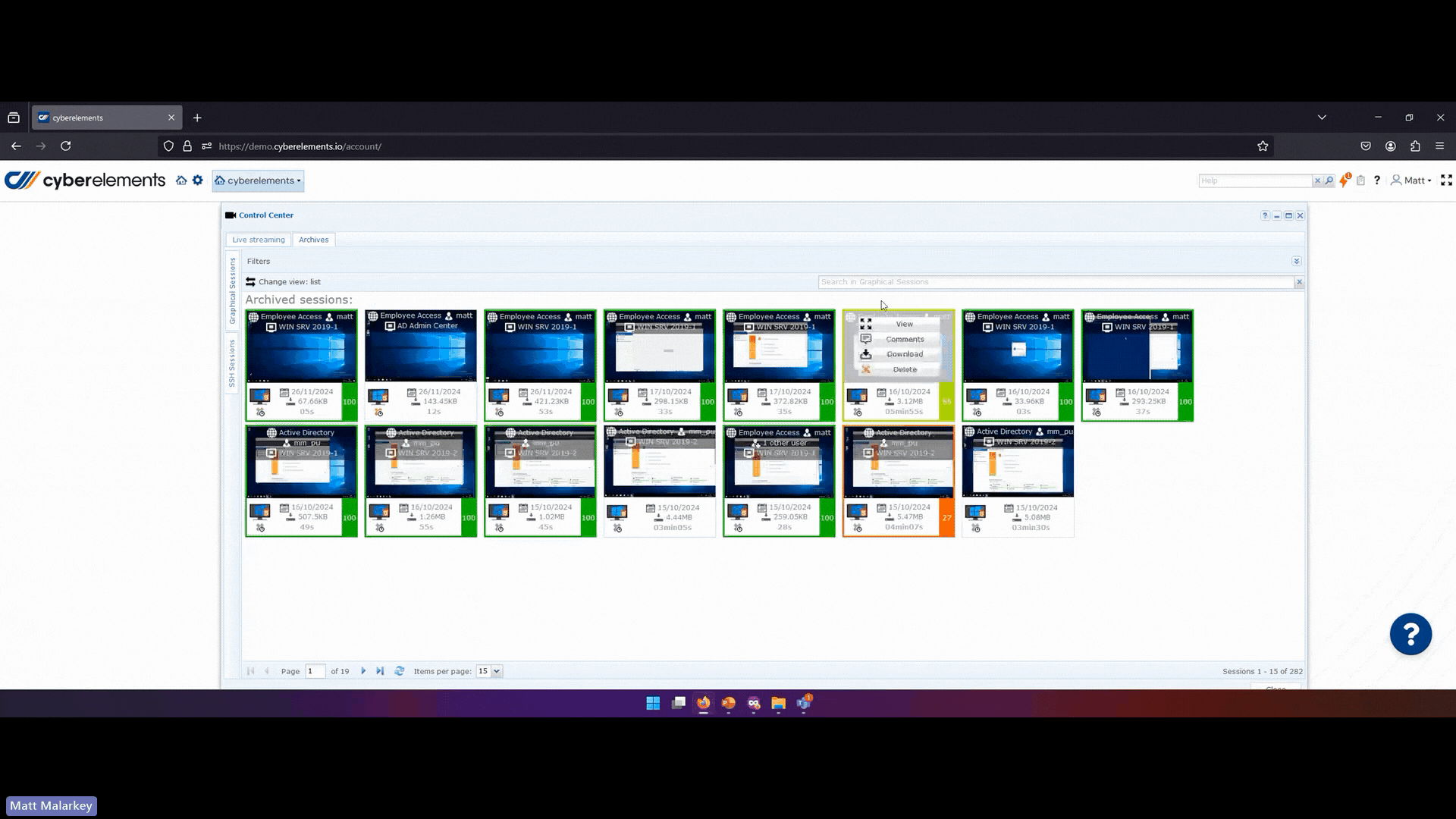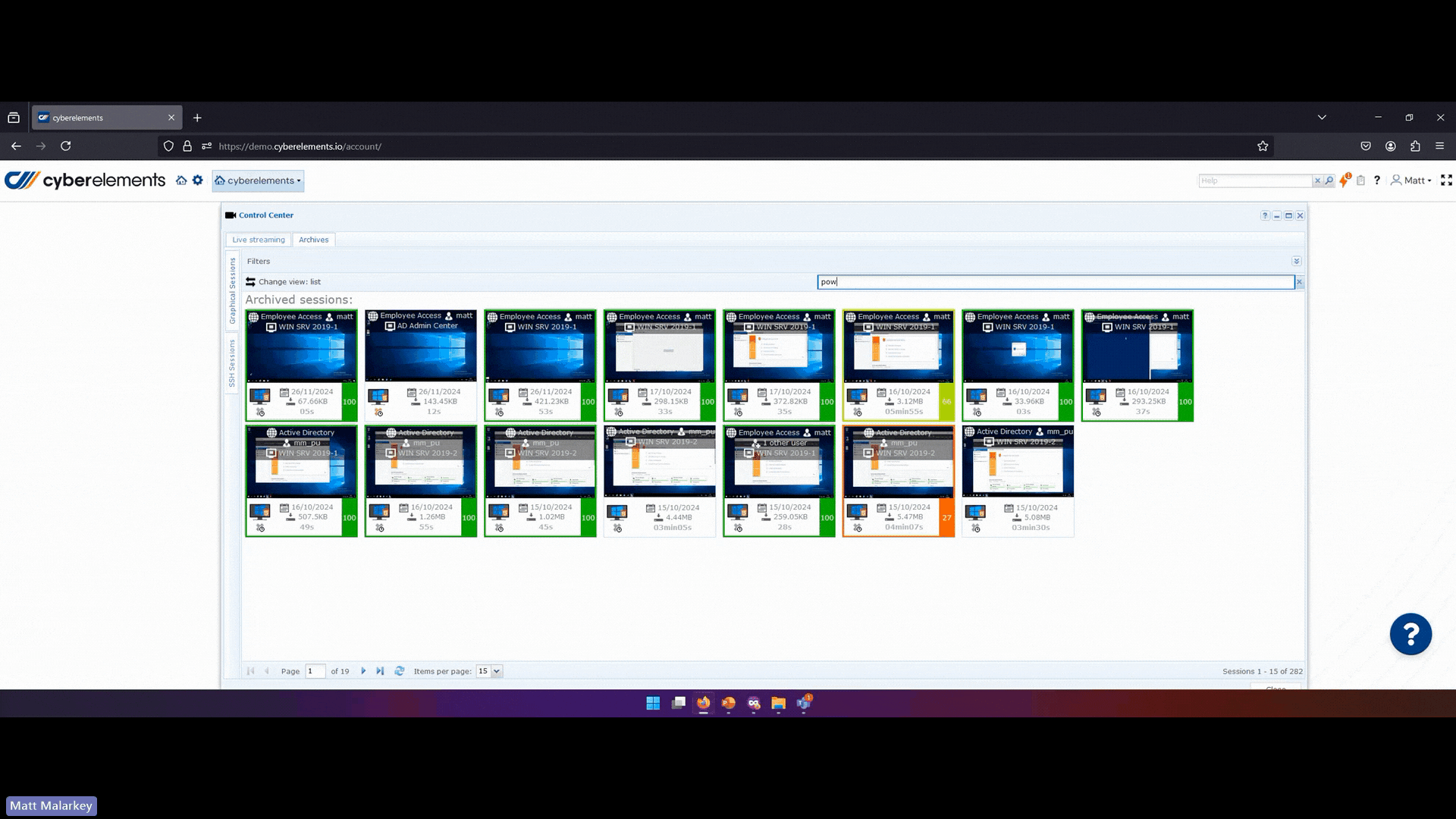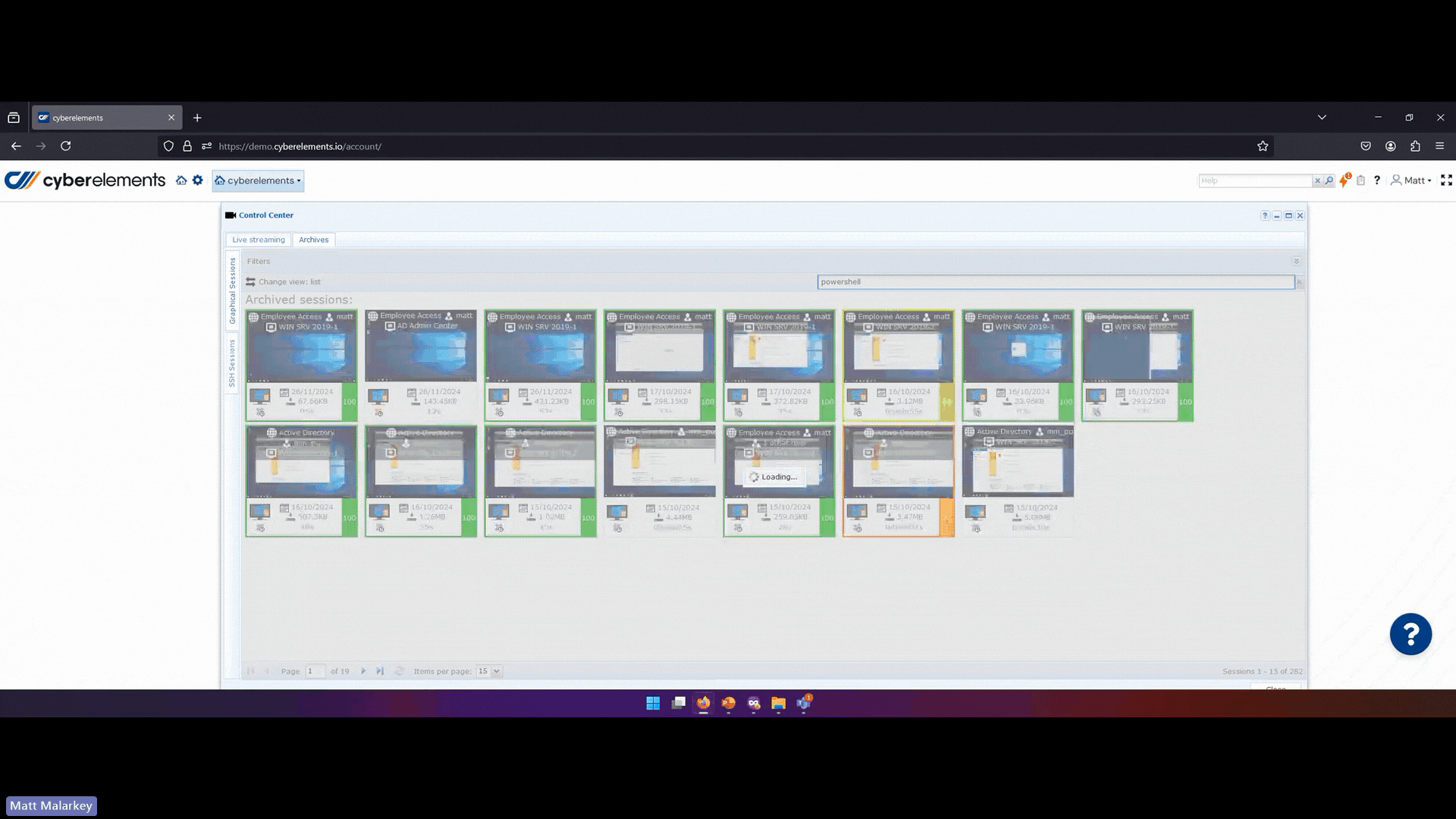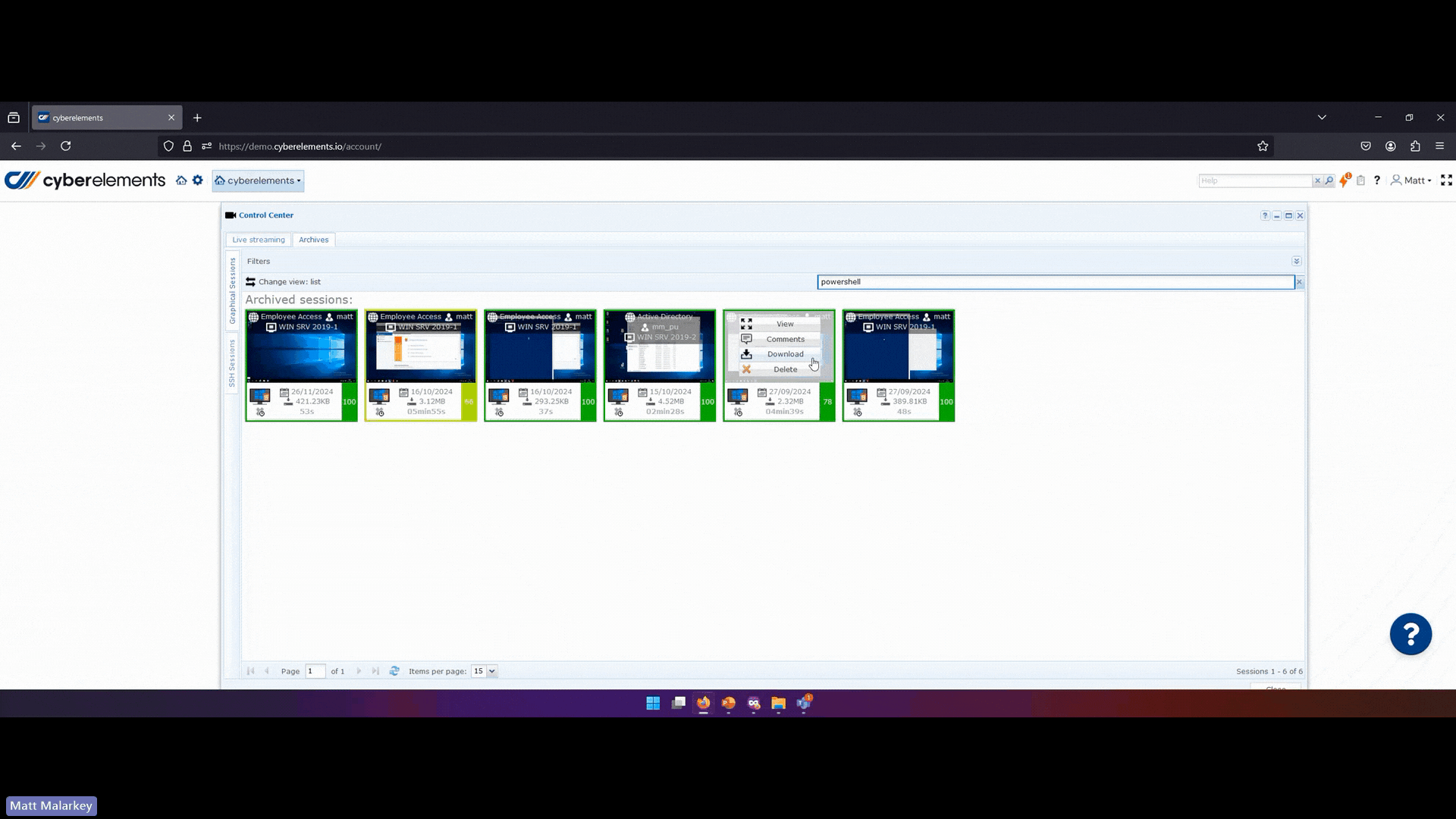
- Leveraging collected data for adaptive security:
cyberelements provide full logs of who connected to which resource at what time ,from which device, to do what. For privileged access, full session recordings are saved in a video format allowing organizations to perform advanced audits and to detect suspicious activities with advanced search.
The cyberelements Advantage
cyberelements not only aligns with the NIST Zero Trust framework but extends its principles with unique capabilities:
- Zero Exposure Architecture: Resources remain invisible to attackers, with no open ports or direct access to applications.
- Granular Policy Enforcement: Every session and action is governed by real-time policies tailored to the user and device context.
- Scalability and Efficiency: cyberelements’ lightweight design ensures security doesn’t come at the cost of performance, even in large, complex environments.
Zero Trust is more than a strategy; it’s a transformation in how we think about and implement security. By mapping directly to NIST’s core and advanced tenets, cyberelements provides organizations with the tools they need to implement Zero Trust effectively.
With cyberelements, businesses can embrace the future of security—dynamic, adaptive, and built for resilience.
Would like to go further? Let’s discuss your access security contact us now