Start your Zero Trust journey
With cyberelements, a Zero Trust Privileged Remote Access Management solution securing your unmaged endpoints.
Invincibility of Unmanaged Endpoints
cyberelements.io ensures the invincibility of your organization’s unmanaged endpoints by applying Zero Trust principles to secure privileged remote access.
Grant access based on user identity and security posture of any used device whether it is company owned or not. cyberelements turns untrusted devices into trusted devices.
Securely connect your privileged users, and third parties to their resources and applications via one convereged Zero Trust platform.
Zero Trust Privileged Access
Workforce & Third Party Access
Complete Isolation of IT & OT Systems
How to Choose Your Privileged Access Management Solution
It is crucial to control the access to industrial Operational Technologies (OT) as it can have a high impact on our real life.
The cyberelements Key Features
Go Passwordless and Deviceless with
Behavioral Biometric Authentication
cyberelements introduces the Behavioral Biometric Authentication revolutionalizing access security.
Rely no more on static passwords or easily lost tokens, choose a more secure and user-friendly authentication method.
The cyberelements system analyses your users’ unique behaviors as they interact with their devices. Different behavioral imprints are then created to identify each user based on the collected data. At time of use, a new pattern is computed and compared against the user’s reference imprint. The system keeps learning over time to improve the reference imprint.
Discover how it works in this video →
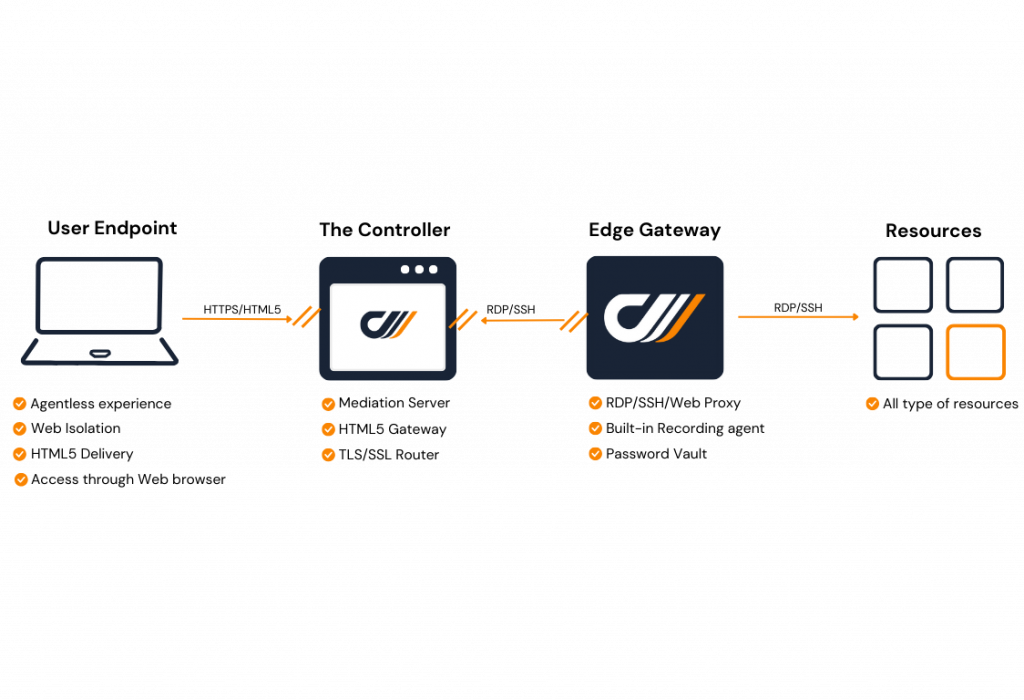
Double Barrier Architecture
for Privileged Remote Access
The Controller: The cyberelements cloud which is a securely isolated entry point. Your IT system is not exposed to the Internet.
The Edge Gateway: Virtual or physical appliance, deployed at the closest to the resources. It acts as a secure relay to the resources whether they are in the cloud or on-premise.
When the user connects to The Controller, The Edge Gateway initiates an on-demand outgoing connection to The Controller. It creates an encrypted tunnel between the Edge Gateway and the Controller.
And it is only when the user connects to a resource that the connection to the resource is created, within the encrypted tunnel, with dynamic ports to protect against brute force attack.
The double barrier architecture is an intrinsic characteristic of a Zero Trust infrastructure and an enabler for your Zero Trust journey.
cyberelements.io served as a bedrock of our Zero Trust journey. It allowed us to give a secure remote access to our privileged users. In an era of cloud resources and remote work, cyberelements provided us with the opportunity to enforce strict access policies thanks to its granular control.
Clientless and serverless
web session recording
Offer a seamless experience to your users by providing a single point of access where all their resources are grouped.
The cyberelements recording feature captures user interactions during sessions involving critical resources and saves them in a video format.
The system automatically detects and stops any suspicious or unauthorized activities in real-time.
Have access to recorded sessions at any time for auditing, investigation, or forensic analysis purposes.
cyberelements, a single portal with built-in:
Single
Sign-On
Password
Vault
Real Time
Analysis
Go clientless with cyberelements
- Connect your users through a web portal to their necessary resources, using any device.
- Go agentless with cyberelements and minimize contamination risks by eliminating any interaction between the connected devices and the organization's resources & systems.
- Enhance access security with our protocol break technology to stop threat propagation.
- The cyberelements HTML5 Gateway puts an end to the web protocol used, extract the information and use it in a new different protocol to access the target resource (RDP, SSH, HTTP, etc.).
Trusted by Thousands of Businesses
cyberelements is a proven solution for securing access to our sensitive data by both internal administrators and external providers. It’s a reliable solution, with 99.99% availability, and has become essential to our company's operations.
Benjamin Pons - CISO @ Corsica Linea
Corsica Linea
Corsica Linea Secure and centralize the management of internal and external access to sensitive servers. Get a Demo Contact Us Corsica Linea > Maritime transport



