Securing 3rd Party Contractor Access
to IT/OT with Remote PAM
Organizations today increasingly rely on third-party contractors for IT and operational technology (OT) system support, maintenance, and upgrades. While this workforce model provides flexibility and access to specialized skills, it also presents significant IT security challenges. Contractors often require access to sensitive systems and data, making them a potential target for cyber threats. Ensuring that 3rd party access is secure, auditable, and aligned with organizational policies is a complex task.
In this article, we’ll explore the key challenges of contractor access and discuss how Remote Privileged Access Management (PAM) can address these issues.
Challenges
Third-party contractors often require access to sensitive IT/OT systems, databases, and applications to perform their tasks. However, this access can create security vulnerabilities due to:
Inadequate Access Management
Contractors often require elevated privileges to perform their tasks. However, without robust access management, they might be granted excessive permissions, leading to unnecessary exposure of sensitive systems. This creates opportunities for intentional or accidental misuse.
Identity Management and Authentication
Verifying the identity of remote contractors and ensuring adequate authentication can be complex for organizations to manage. Traditional methods of identity verification are often inadequate for ensuring only authorized individuals gain access.
Compliance Risks
Traditional access solutions might not provide granular audit trails, making it difficult to track contractor activities. This lack of visibility can result in non-compliance with regulations such as NIS 2.
Lack of Visibility and Control
Many organizations struggle to monitor and control contractor activities once access is granted. This lack of visibility can lead to unintentional violations of security policies or malicious threats.
Increased Attack Surface
Granting third-party access exposes and increases the organization’s attack surface. Contractors may use unsecured devices, operate from less-secure networks, or lack rigorous cybersecurity practices, creating potential entry points for cyber threats.
Scalability and Time Constraints
Managing access for multiple contractors can overwhelm IT teams. Granting and revoking access quickly while ensuring security becomes a logistical challenge.
What is Remote PAM
Remote PAM solutions are purpose-built to manage and secure privileged access for remote users, including 3rd-party contractors. These solutions address the above challenges through advanced features and capabilities.
cyberelements is a SaaS based Remote PAM solution dedicated to solving these business challenges.
Access Management
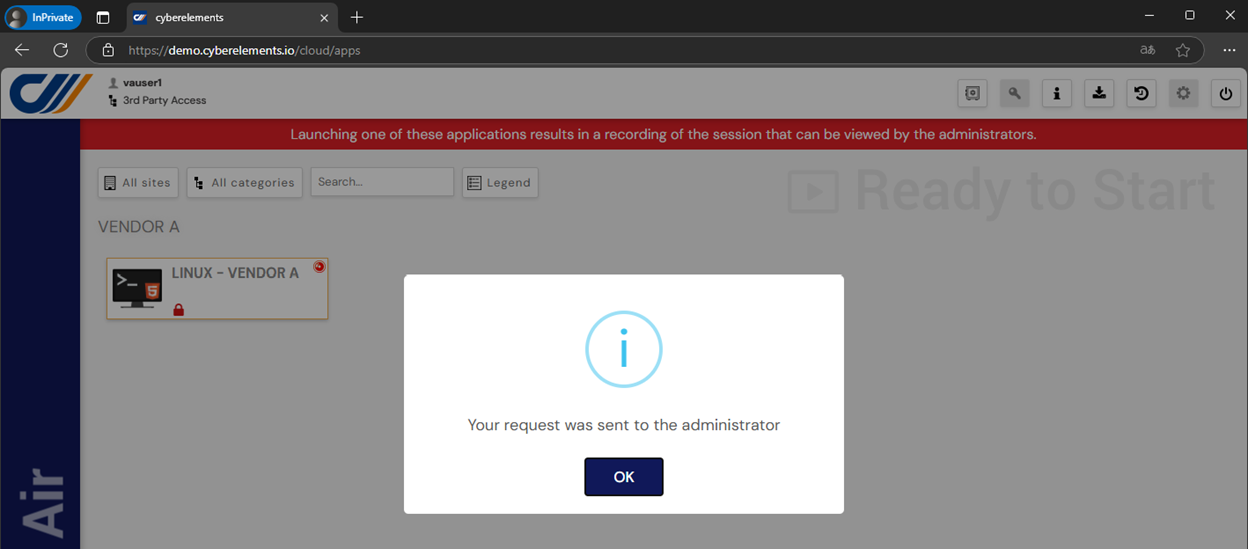
Access Policies
cyberelements Access policies allow organizations to deploy the ‘zero trust’ approach to privileged access enabling granular access control ensuring a ‘least privileged’ approach minimizing the risk of unauthorized access. This ‘default’ access rule defines who has access to what resources. In addition to this a ‘dynamic’ access condition can be applied which can grant access based on real time context of the user connection.
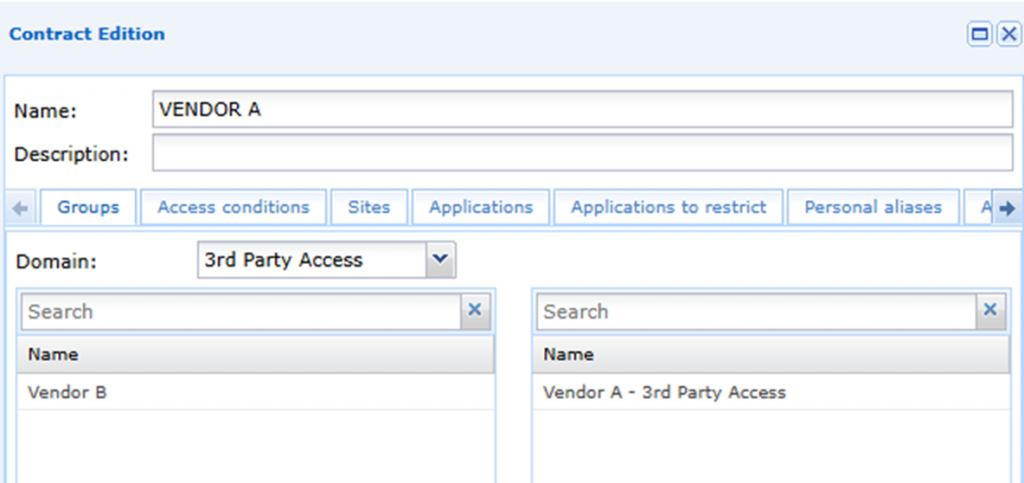
Password Vault
Elevated (Admin) privileges are managed using the password vault enabling the organization to manage their privileged identities centrally in an encrypted vault and inject them on-demand into target applications. The user (3rd-party contractor) does not have access to the credentials therefore they cannot be exposed from the vendor in the event the 3rd party is compromised.
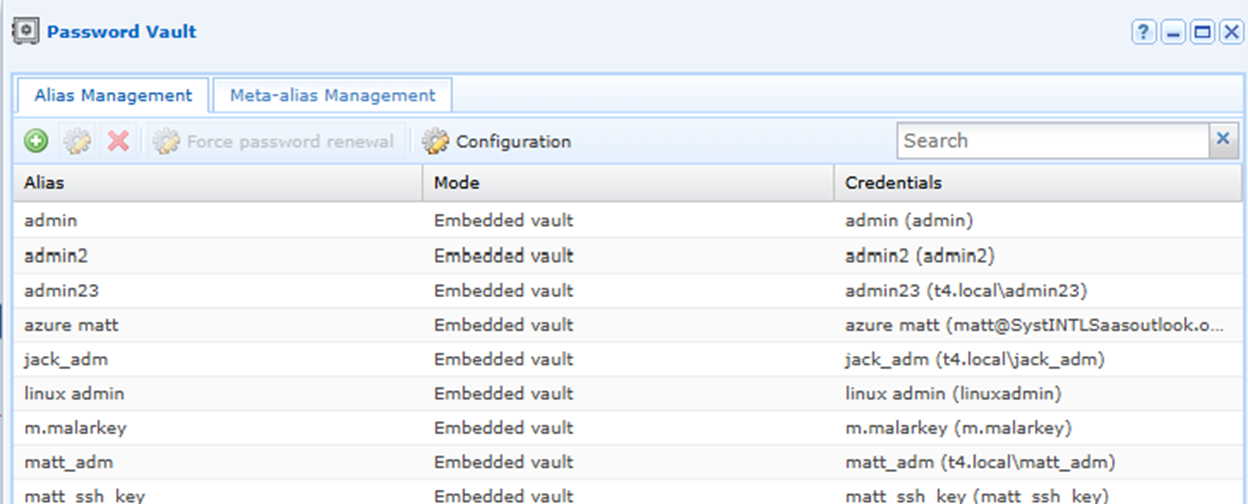
Identity Management
Identity Providers
Connect and synchronize to your existing user directories or use dedicated local identities for 3rd-party access. In this case the credentials provided to the 3rd-party can ONLY be used for the purpose of logging in to the cyberelements Remote PAM platform reducing the exposure of the organization.

MFA
Integrated MFA allows for verification of the identity of the contractor before granting access, so even if the account credentials are compromised, unauthorized access is prevented. cyberelements provides multiple options for MFA including SMS/Email OTP, Mobile Authenticator TOTP and integration with 3rd party authentication protocols e.g. SAML / FIDO2.
Compliance
Session Recording & Activity Logs
All sessions are recorded allowing video playback and advanced search on contractor activities. In addition, all access is logged and automated reports can be generated and delivered to relevant stakeholders.
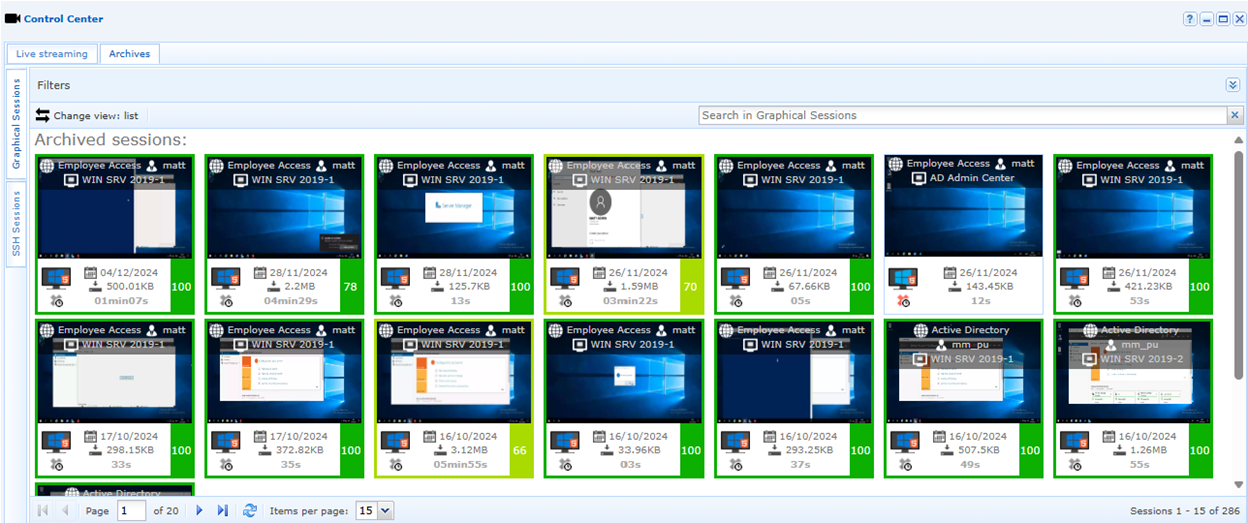
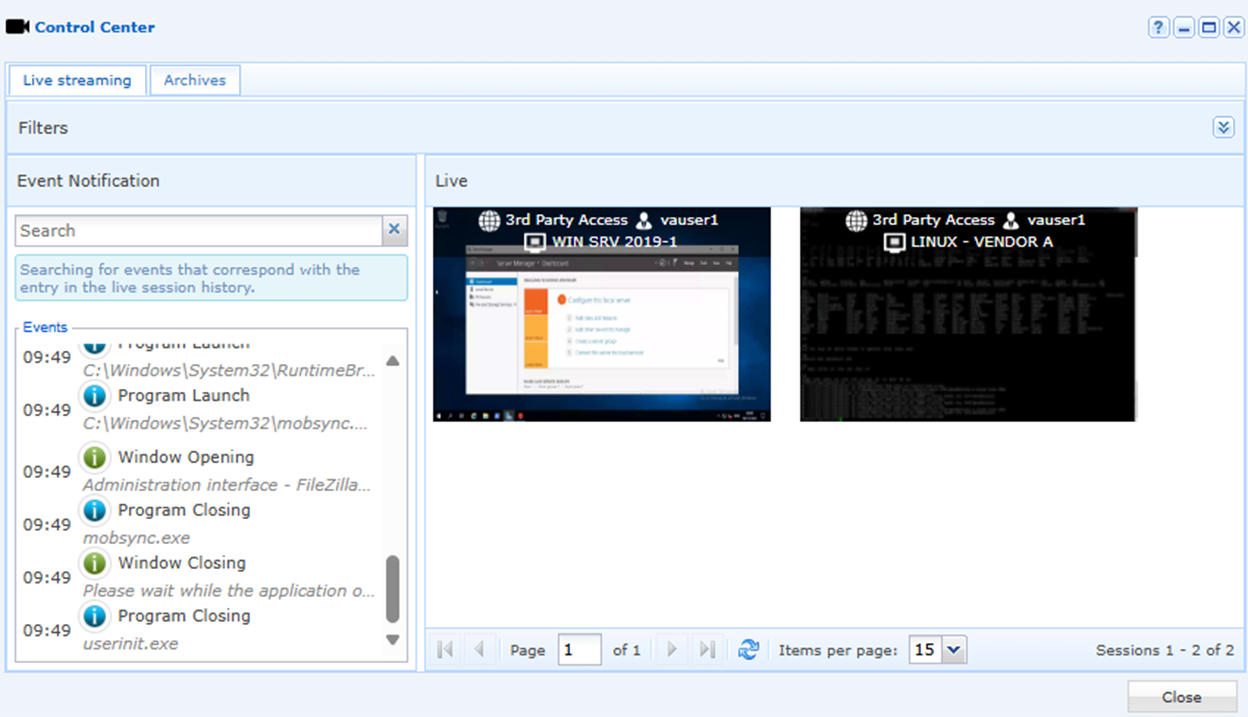
Visibility and Control
Live Streaming
Real-time monitoring and recording of contractor sessions provides complete visibility into their activities. Organizations can interact in real-time to stop malicious activities or interact with contractor’s sessions using the 4 hands feature. With the 4 Hands feature a contractor could invite a local administrator into a session or vice versa, thus allowing for the principal of ‘4 eyes’ approval but with the additional functionality of the ‘4 hands’ interaction.
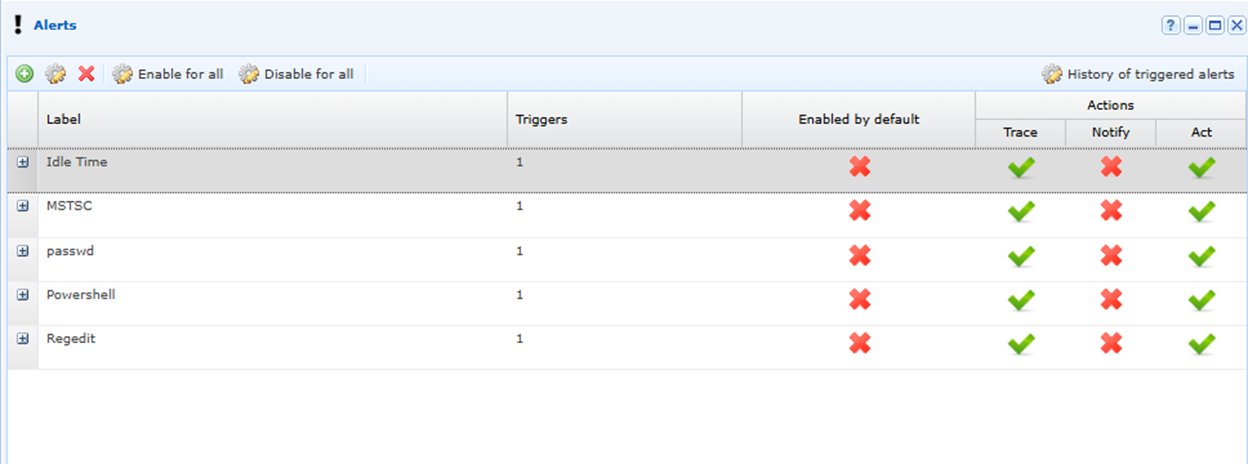
Alert Management
Organizations can set up alerts as part of a detect and response feature of the platform. The alert definition consists of the detection of events such as process launches, commands, keystrokes which triggers an automated response in real time. For example, the contractor is connected to a windows session and tries to run powershell. An alert can detect this process launch and provide an automated ‘live’ response, locking the contractor’s session until a super admin validates the activity.
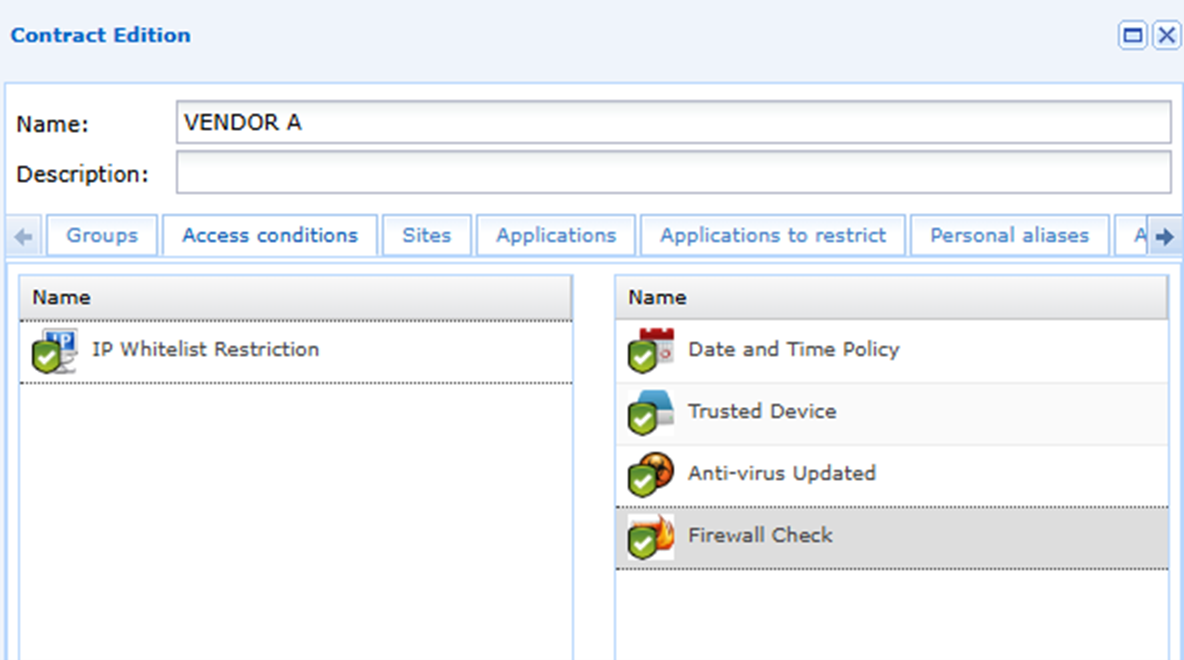
Endpoint Control
Access Conditions
Limit the organizations exposure to untrusted devices by defining Access conditions to check the integrity of the endpoints prior to connection. This ‘dynamic access rule’ works in addition to the default access policy providing contextual access for the user connection.
Clientless, Web-browser only
Further protect exposure to 3rd party devices by utilizing the HTML5 ‘clientless’ access which provides a ‘protocol break’ avoiding the propagation of threats (malware, ransomware etc) between the 3rd party endpoint and the organizations IT systems. This protocol break in effect enables trusted access from untrusted devices.
Scalability and Time Constraints
Workflow / JIT
Grant contractors access only for the duration of their tasks and upon approval by a supervisor using the zero-trust least privilege principle. With this feature the contractor requests access, this generates an approval request, which a supervisor can then decide on the level of access required. i.e. one-time connection or approval for a duration of time. When completed, access is automatically revoked, reducing the risk of unauthorized access.