How To Increase The Size of The /var Partition on Virtual Appliances
How To? How To Increase The Size of The /var Partition on Virtual Appliances This article describes how to extend an LVM partition on cyberelements’
A workflow is a just in time (JIT) access request to specific resources. In addition to the access request feature, the administrator can define access conditions for a set of resources.
The administrator can have full control access to resources that are considered critical and for which an access notifcation is required. Therefore, access is only granted after human approval.
cyberelements offers many access restriction possibilities. In section we are going to learn how to use and implement the workflow mechanism in cyberelements.
First, we need to choose the concerned users group, sites, and resources in the admin console.
Once the resources that need to be restricted are identified, you need to create access contracts in the Access Policies section:
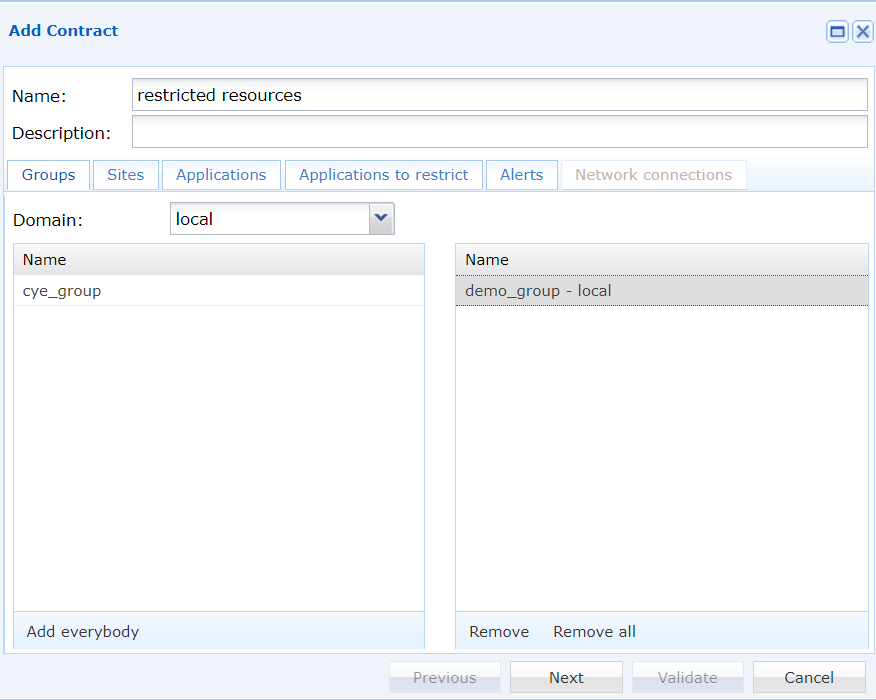
First, you will need to choose the users group which will be able to see the selected resources on the cloud portal.
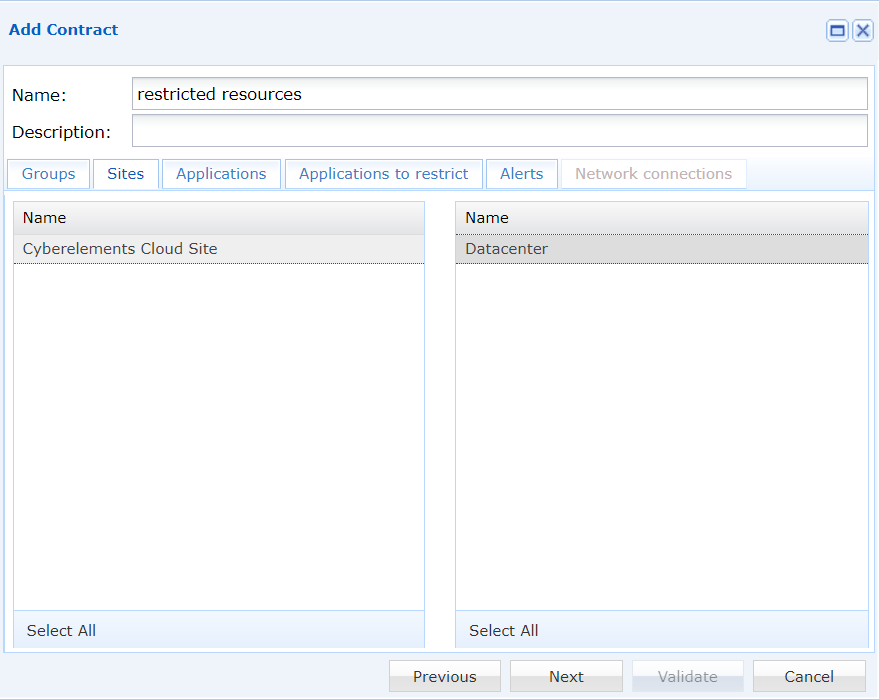
Select the site that allows access to the resources.
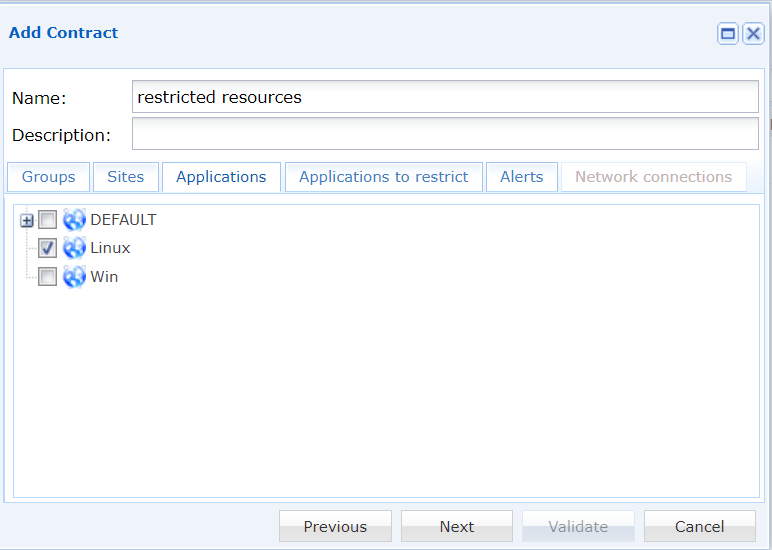
Select the resources that you would like to appear on the portal for the chosen group of users.
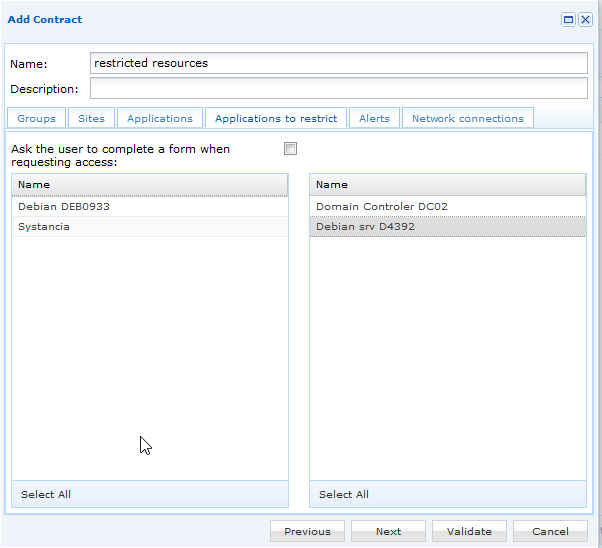
Select the resources that will require the administrator’s permission to access and click the Validate button.
Now you have the access request workflow up and running. Let’s check how does it work.
When users are logged in, they will now have the restricted resources (that require the administrator’s authorisation) in red.
When users click on restricted resources, the following message will appear.
If the request is accepted, several options are available. click on the question mark icons in the following image to learn more about each option.
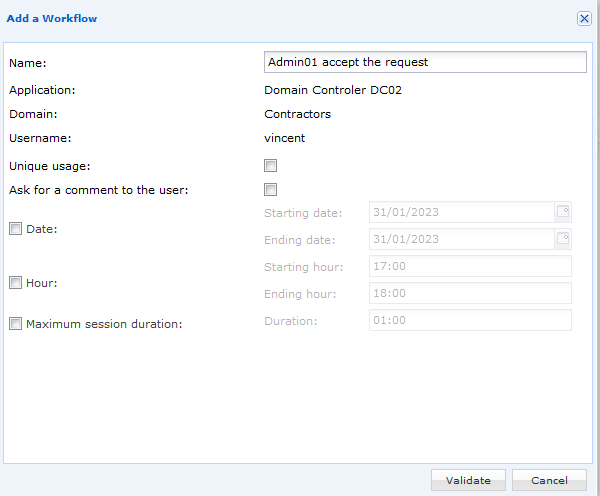
Unique Usage:
The user can only launch the resource once.
If the user wants to run it again,
a second access request need to be made.
Ask for a comment to the user:
When the resource is opened,
the user will be asked for a comment
(e.g. for the reason for connection).
This comment will be displayed in
the video archive afterwards.
Date:
It is the date when the user can open the resource.
After the deadline, the user will not longer be able to start the
resource and will have to make a new request.
Hour/Time:
It is the time slot where the user is allowed to open the resource.
If the user attempts to launch the resource outside these times,
the user will see a red lock on the resource.
Maximum session duration:
It is the maximum time during which a user can use the resource.
After this period, the user will be automatically logged out.
Once the user’s request is validated, a green check appears under Status.
To obtain more details about the validation request, you can simply go to the Workflow Tab.
Once a request is validated by the administrator, a green padlock will appear in the user account.
By default, there are no email alerts configured to notify the administrator that the request has been made. However, you can set it up in the admin console. For that, you will need an SMTP server configured.
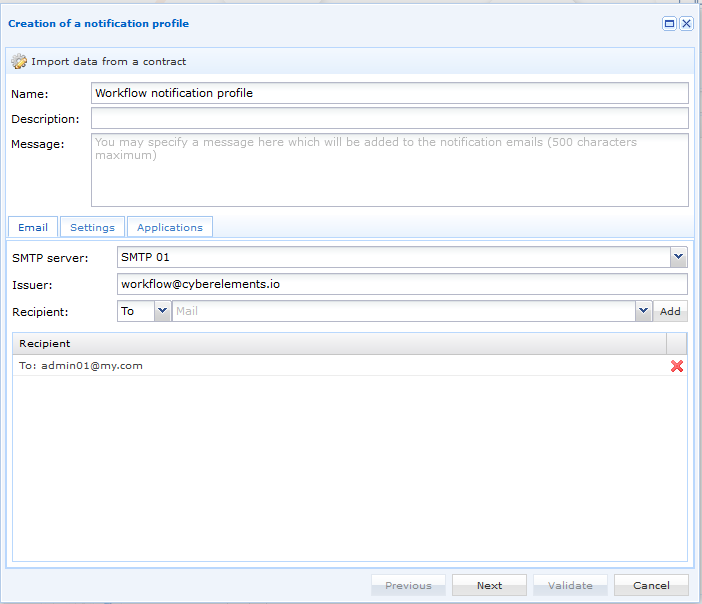
Once the SMTP server is configured, we need to define and set up a notification profile.
First, you will need to choose the users group which will be able to see the selected resources on the cloud portal.

First, fill in the SMTP server, sender and recipient(s) of the mail:
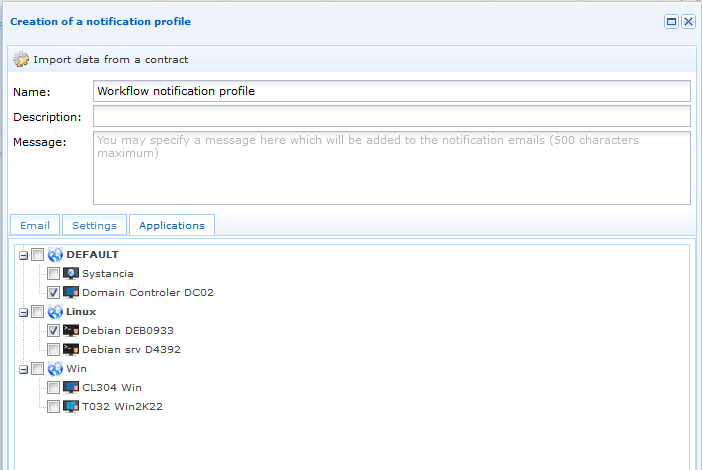
In the “Resources” tab, check the concerned resources, and click “validate“.
With the Resource Access Request feature, you can now have full control on critical resources. Our experts highly recommend using this feature to manage access and increase the security level.
Would like learn more? Book a meeting with our experts
Try the Just in Time feature in cyberelements
or book a meeting with our experts
Related Articles
How To? How To Increase The Size of The /var Partition on Virtual Appliances This article describes how to extend an LVM partition on cyberelements’
How To? Securely Transfer Files in cyberelements In this article we will explain how to transfer files in cyberelements. This article describes the various methods
How To? Configure an SMTP Server The cyberelements platform allows to receive alerts, notifications and OTPs by e-mail via an SMTP server integrated into the
How To? Transfer the password vault’s database to another server? This article explains how to move the database of the embedded vault containing the various
How To? Implement authentication with FIDO2 keys This article describes how to implement authentication with FIDO2 biometric security keys in cyberelements. The content of this
How To? Set Up an OTP Mail? This article describes how to set up secure access to the cyberelements platform using OTP mail. The OTP